Raspberry Robin Malware Upgrades with Discord Spread and New Exploits Feb 09, 2024 Newsroom Malware / Dark Web The operators of Raspberry Robin are now using two new one-day exploits to achieve local privilege escalation, even as the malware continues to be refined and improved to make it stealthier than before. This means that “Raspberry Robin has access to an ...
Read More »Monthly Archives: February 2024
Alert: New Stealthy
Alert: New Stealthy Feb 10, 2024 Newsroom mac OS Malware / Cyber Threat Apple macOS users are the target of a new Rust-based backdoor that has been operating under the radar since November 2023. The backdoor, codenamed RustDoor by Bitdefender, has been found to impersonate an update for Microsoft Visual Studio and target both Intel and Arm architectures. The exact ...
Read More »Warning: New Ivanti Auth Bypass Flaw Affects Connect Secure and ZTA Gateways
Warning: New Ivanti Auth Bypass Flaw Affects Connect Secure and ZTA Gateways Feb 09, 2024 Newsroom Vulnerability / Zero Day Ivanti has alerted customers of yet another high-severity security flaw in its Connect Secure, Policy Secure, and ZTA gateway devices that could allow attackers to bypass authentication. The issue, tracked as CVE-2024-22024, is rated 8.3 out of 10 on the ...
Read More »After FBI Takedown, KV-Botnet Operators Shift Tactics in Attempt to Bounce Back
After FBI Takedown, KV-Botnet Operators Shift Tactics in Attempt to Bounce Back The threat actors behind the KV-botnet made “behavioral changes” to the malicious network as U.S. law enforcement began issuing commands to neutralize the activity. KV-botnet is the name given to a network of compromised small office and home office (SOHO) routers and firewall devices across the world, with ...
Read More »Critical Patches Released for New Flaws in Cisco, Fortinet, VMware Products
Critical Patches Released for New Flaws in Cisco, Fortinet, VMware Products Feb 08, 2024 Newsroom Cyber Threat / Network Security Cisco, Fortinet, and VMware have released security fixes for multiple security vulnerabilities, including critical weaknesses that could be exploited to perform arbitrary actions on affected devices. The first set from Cisco consists of three flaws – CVE-2024-20252 and CVE-2024-20254 (CVSS ...
Read More »Kimsuky’s New Golang Stealer ‘Troll’ and ‘GoBear’ Backdoor Target South Korea
Kimsuky’s New Golang Stealer ‘Troll’ and ‘GoBear’ Backdoor Target South Korea Feb 08, 2024 Newsroom Cyber Espionage / Malware The North Korea-linked nation-state actor known as Kimsuky is suspected of using a previously undocumented Golang-based information stealer called Troll Stealer. The malware steals “SSH, FileZilla, C drive files/directories, browsers, system information, [and] screen captures” from infected systems, South Korean cybersecurity ...
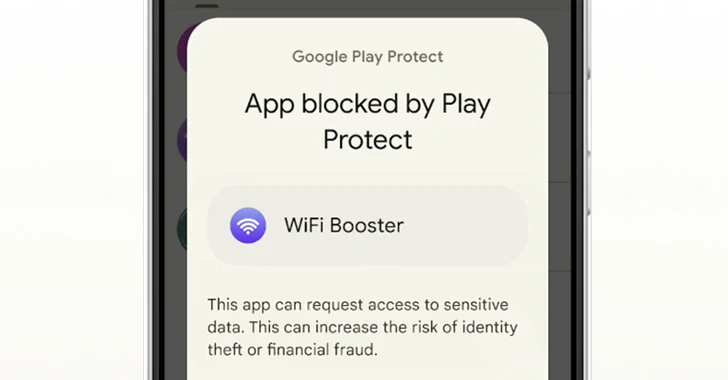
Read More »Google Starts Blocking Sideloading of Potentially Dangerous Android Apps in Singapore
Google Starts Blocking Sideloading of Potentially Dangerous Android Apps in Singapore Feb 08, 2024 Newsroom Data Protection / Mobile Securit Google has unveiled a new pilot program in Singapore that aims to prevent users from sideloading certain apps that abuse Android app permissions to read one-time passwords and gather sensitive data. “This enhanced fraud protection will analyze and automatically block ...
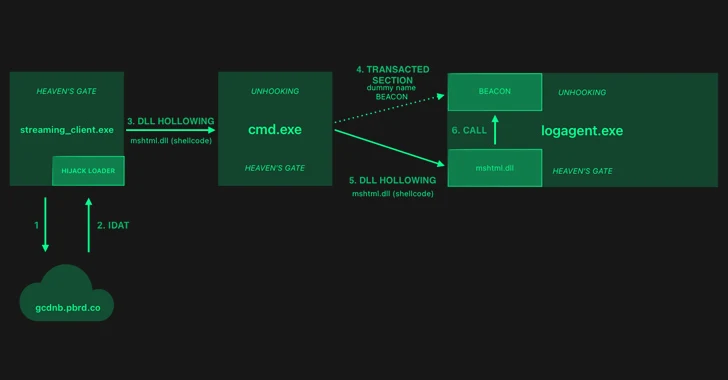
Read More »HijackLoader Evolves: Researchers Decode the Latest Evasion Methods
HijackLoader Evolves: Researchers Decode the Latest Evasion Methods Feb 08, 2024 Newsroom Endpoint Security / Cyber Threat The threat actors behind a loader malware called HijackLoader have added new techniques for defense evasion, as the malware continues to be increasingly used by other threat actors to deliver additional payloads and tooling. “The malware developer used a standard process hollowing technique ...
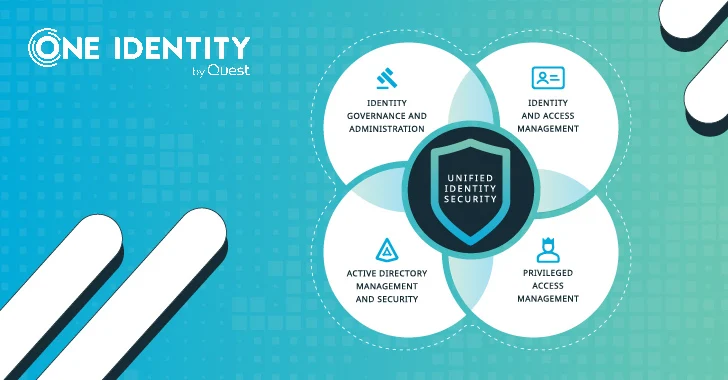
Read More »Unified Identity – look for the meaning behind the hype!
Unified Identity – look for the meaning behind the hype! Feb 08, 2024 Unified Identity / Cyber Security If you’ve listened to software vendors in the identity space lately, you will have noticed that “unified” has quickly become the buzzword that everyone is adopting to describe their portfolio. And this is great! Unified identity has some amazing benefits! However (there ...
Read More »Chinese Hackers Operate Undetected in U.S. Critical Infrastructure for Half a Decade
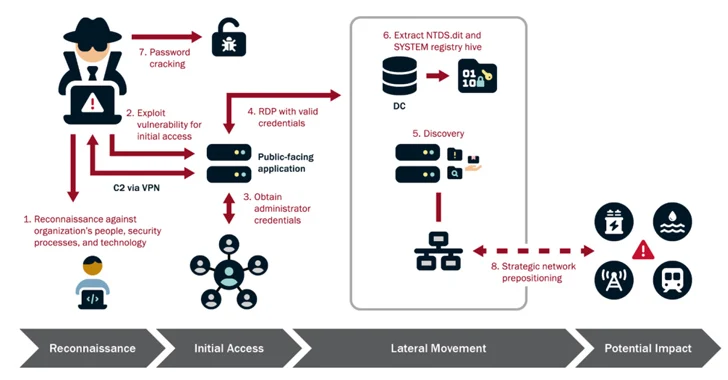
Chinese Hackers Operate Undetected in U.S. Critical Infrastructure for Half a Decade The U.S. government on Wednesday said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some critical infrastructure networks in the country for at least five years. Targets of the threat actor include communications, energy, transportation, and water and wastewater systems sectors in the ...
Read More » Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India