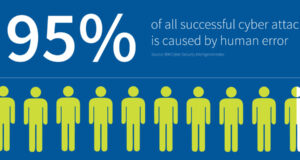
Why Human Error is #1 Cyber Security Threat to Businesses in 2023 Phishing and Malware Among the major cyber threats, the malware remains a significant danger. The 2017 WannaCry outbreak that cost businesses worldwide up to $4 billion is still in recent memory, and other new strains of malware are discovered on a daily basis. Phishing has also seen a ...
Read More »Firewall
A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems
A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems German authorities last week disclosed that a ransomware attack on the University Hospital of Düsseldorf (UKD) caused a failure of IT systems, resulting in the death of a woman who had to be sent to another hospital that was 20 miles away. The incident marks the first recorded casualty as a ...
Read More »What is a Next Generation Firewall (NGFW) ?
What is a Next Generation Firewall? Learn about the differences between NGFW and traditional firewalls Firewalls are a standard security tool for the majority of companies, but in today’s changing threat landscape, next generation firewalls are the only firewalls that can provide proper protection. A Definition of Next Generation Firewall A next generation firewall (NGFW) is, as Gartner defines it, ...
Read More »Firewalls
TOP Firewall Brands IT Monteur’s Firewall Firm is the TOP Firewall providers company in India is authorized partner for more than 12 hardware Firewall manufacturer of the world & Cloud Firewall providers like AWS, Microsoft, Google Juniper Firewall Models Cisco Firewall Models Checkpoint Firewall Models Palo Alto Firewall Models Fortinet Firewall Models Forcepoint Firewall Models Sophos Firewall Models Watchguard ...
Read More »FORTINET Fortigate 40F
FORTINET Fortigate 40F Buy FORTINET Fortigate 40F Firewall online from IT Monteur store The FortiGate/FortiWiFi 40F series provides a fast and secure SD-WAN solution in a compact fanless desktop form factor for enterprise branch offices and mid-sized businesses. Protects against cyber threats with system-on-a-chip acceleration and industry-leading secure SD-WAN in a simple, affordable, and easy to deploy solution. Fortinet’s Security-Driven ...
Read More »WatchGuard Firebox T35
WatchGuard Firebox T35 WatchGuard Firebox T35 with 3-yrs Basic Security Suite Rs 87380.00 INR Buy WatchGuard Firebox T35 online from IT Monteur Store Big Security for Small Businesses Small businesses and remote locations have long been thought of as soft targets for attackers. WatchGuard Firebox T35 and T55 tabletop appliances bring enterprise-level network security to those small office/branch office and ...
Read More »Sophos XG 115
Sophos XG 115 Sophos XG 115 Firewall Hardware with 3 year License Rs 64540.00 Buy Sophos XG 115 Hardware Firewall with 3 year license online from IT Monteur Store XG Series Firewall Appliances Our XG Series hardware appliances are purpose-built with the latest multi-core Intel technology, generous RAM provisioning, and solid-state storage. Whether you’re protecting a small business or a ...
Read More »WatchGuard Firewall Support India
WatchGuard Firewall Support Services Provider in India WatchGuard Firewall Support WatchGuard is an advanced technology-based firewall that offers an exceptional level of security to your system. In the event, if a WatchGuard firewall user faces any issue, they can share their queries at WatchGuard firewall support services. Here, are the professionals round the clock available for the customers to troubleshoot ...
Read More »SonicWall Firewall Support India
SonicWall Firewall Support Services Provider in India SonicWall Firewall Support SonicWall Firewall Support Are you using Sonicwall firewall and facing some issues regarding it? If yes, then you have reached the right place. We are one of the prominent SonicWall firewall support service providers, who always readily available to resolve the technical issues that you are facing right now. The ...
Read More »Firewall Consultant
Firewall Consultants in India An up-to-date firewall can help you protect your organization’s network while allowing legitimate business communication to be sent and received. It keeps bad actors out and can be used to keep employees away from insecure or non-work-related sites. While a firewall provides excellent security and protection, it needs monitoring and management. Monitoring your own firewall ...
Read More » Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India