TOP Firewall Brands
IT Monteur’s Firewall Firm is the TOP Firewall providers company in India is authorized partner for more than 12 hardware Firewall manufacturer of the world & Cloud Firewall providers like AWS, Microsoft, Google
IT Monteur’s Firewall Firm is the TOP Firewall providers company in India is authorized partner for more than 12 hardware Firewall manufacturer of the world & Cloud Firewall providers like AWS, Microsoft, Google

Hire a Firewall Engineer
An up-to-date firewall can help you protect your organization’s network while allowing legitimate business communication to be sent and received. It keeps bad actors out and can be used to keep employees away from insecure or non-work-related sites.
While a firewall provides excellent security and protection, it needs monitoring and management. Monitoring your own firewall is a time-consuming, intensive, and expensive task that requires security expertise and regular upgrades. Many organizations lack the internal expertise, time, and capital to monitor their own firewalls around-the-clock. For these companies, a managed firewall is an affordable, effective solution.
Managed Firewall Service in India
A managed firewall is a service that offers enhanced threat management. Security experts monitor your firewall remotely and can help mitigate any potential threats. To accomplish this, they study your network traffic and learn what normal traffic looks like for your business. When any unusual activity is detected, it can be quickly identified and addressed.
In addition, your provider will perform routine traffic analysis and send regular reports to you so you will have a clear sense of your network traffic patterns and how your managed services team is managing threats to your network.
The beauty of IT services like managed firewall is their ability to leverage economies of scale to offer companies the cybersecurity they need, at a price they can afford. In the past, your only option was to create an in-house security solution for your network, which you had to pay for through a capital expenditure.
Here are 3 ways a managed firewall can enhance your company’s operations:

Protect against Cyber Crime
Cyber crime is a growing concern for businesses and citizens alike. According to a recent cyber crime report published by research firm Cybersecurity Ventures, cyber attack rates are climbing faster than any other crime and will cost the global economy $6 trillion annually by 2021.
A business that falls prey to a cyber criminal will face serious losses and a tough road ahead. According to a 2017 report published by the Better Business Bureau, half of all businesses would lose their profitability within a month if their critical data was lost.
With a managed firewall, business owners can avoid or mitigate the risk of a cyber attack or breach.

Meet compliance requirements
As the threat level of cyber attacks continues to grow, so does the burden of compliance regulations. Existing regulations such as HIPAA, PCI DSS, and Sarbanes Oxley continue to evolve with ever stricter and more technical compliance requirements. New regulations such as GDPR add to the complexity.
A managed firewall service provider with compliance expertise can ensure your company meets these legal requirements, avoiding the heavy penalties associated with negligence.
Ease burden of monitoring
The burden of round-the-clock monitoring can be heavy for many SMBs. For example, if you have a small IT department with just one security expert, it’s not possible for your staff to continuously monitor your network.
Most business owners need to stay focused on their core business activities; they don’t have time to become IT security experts. And hiring enough staff for 24/7 monitoring may be too expensive. A managed firewall solution solves both of these problems.
With the support of Managed Edge Security from Firewall Firm, you can shift the burden of network security, compliance, and monitoring to our team of security experts. With Firewall Firm’s Managed Edge Security solution, customers benefit from next-generation firewall services and unified threat mitigation to protect their network, Our experts work diligently to stay on top of emerging threats, current best practices, and compliance requirements.
Our security experts will continuously watch your network for anomalies, strange patterns, or any other indicators of potential threats. We can also take on routine tasks, including security updates and patches, to free your internal resources to help you accomplish more important tasks and projects.
We can provide high levels of security for your network and bill you on a monthly basis, as an OpEx. Through a carefully crafted Service Level Agreement (SLA), we will spell out our responsibilities and what you can expect from us in the event of a cyber attack on your network.
Firewalls can protect your network against unauthorized access and intruders.
As enterprises expand its mission-critical networks with newer applications, many have begun to view network security technologies as the key to prevent intrusion and exposure of critical data. Without protection, companies can experience security breaches resulting in serious damages. The security system that all enterprises should seek to implement in such a situation is a firewall. Firewalls are certainly becoming a critical part of any secure network.
The Last one is important and no one configures firewall for that (certification)
Every one is thinking that firewall is now matured and nothing is need more.
But after ransomware things have changed.

24×7 Firewall Monitoring Services in India
Take advantage of our group of dedicated Firewall professionals to manage, monitor and respond to network attacks.
System Management – Allows you to focus on other tasks.
Proactive Security Monitoring – We watch and respond to Internet attacks so you don’t have to.
Network Monitoring – We monitor the firewall to ensure your network stays connected to the Internet.
Change Management Reporting – You will always know what is going on and what we did to fix it.
Customized to Your Needs – You control the level of service that is right for you.
» Best practice configuration
» Unlimited phone support
» Constant access to Web-based monitoring & reporting
» No charge equipment repair or replacement
» Remote firmware updates
» Quick configuration changes
» Outage notice by e-mail
» After hours emergency response from our certified team
» No contract or extended customer commitment!
» This service is provided on a month-to-month basis.
Managed Firewall Support Services in India

Managed Firewall Support Services, Firewall Support Service, Firewall support Services Provider in India
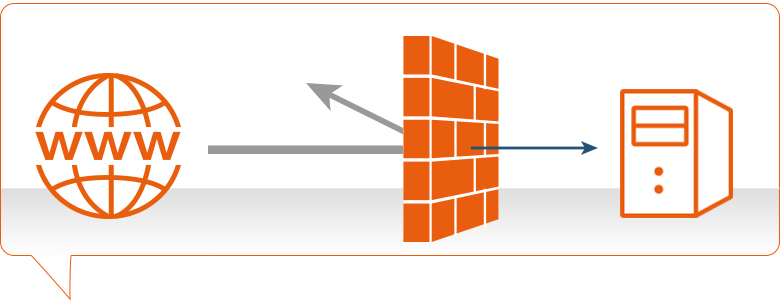
What is Firewall?
Firewall, What is Firewall? A firewall is a network security device located between your internal network and the wider Internet. A firewall monitors incoming and outgoing network traffic – blocking or allowing it based on a set of configurable rules.
Firewalls are a fundamental piece of security and typically form the first line of defense on a network. Acting as a filter against bad connections from the outside world.
A firewall works by comparing the data sent into or out of the network against a list of rules. Based on the results of the rule checking, the firewall will then either block or allow the connection.
A firewall is a system that provides network security by filtering incoming and outgoing network traffic based on a set of user-defined rules. In general, the purpose of a firewall is to reduce or eliminate the occurrence of unwanted network communications while allowing all legitimate communication to flow freely. In most server infrastructures, firewalls provide an essential layer of security that, combined with other measures, prevent attackers from accessing your servers in malicious ways.
This guide will discuss how firewalls work, with a focus on stateful software firewalls, such as iptables and FirewallD, as they relate to cloud servers. We’ll start with a brief explanation of TCP packets and the different types of firewalls. Then we’ll discuss a variety of topics that a relevant to stateful firewalls. Lastly, we will provide links to other tutorials that will help you set up a firewall on your own server.
Before discussing the different types of firewalls, let’s take a quick look at what Transport Control Protocol (TCP) network traffic looks like.
TCP network traffic moves around a network in packets, which are containers that consist of a packet header—this contains control information such as source and destination addresses, and packet sequence information—and the data (also known as a payload). While the control information in each packet helps to ensure that its associated data gets delivered properly, the elements it contains also provides firewalls a variety of ways to match packets against firewall rules.
It is important to note that successfully receiving incoming TCP packets requires the receiver to send outgoing acknowledgment packets back to the sender. The combination of the control information in the incoming and outgoing packets can be used to determine the connection state (e.g. new, established, related) of between the sender and receiver.
Let’s quickly discuss the three basic types of network firewalls: packet filtering (stateless), stateful, and application layer.
Packet filtering, or stateless, firewalls work by inspecting individual packets in isolation. As such, they are unaware of connection state and can only allow or deny packets based on individual packet headers.
Stateful firewalls are able to determine the connection state of packets, which makes them much more flexible than stateless firewalls. They work by collecting related packets until the connection state can be determined before any firewall rules are applied to the traffic.
Application firewalls go one step further by analyzing the data being transmitted, which allows network traffic to be matched against firewall rules that are specific to individual services or applications. These are also known as proxy-based firewalls.
In addition to firewall software, which is available on all modern operating systems, firewall functionality can also be provided by hardware devices, such as routers or firewall appliances. Again, our discussion will be focused on stateful software firewalls that run on the servers that they are intended to protect.
As mentioned above, network traffic that traverses a firewall is matched against rules to determine if it should be allowed through or not. An easy way to explain what firewall rules looks like is to show a few examples, so we’ll do that now.
Suppose you have a server with this list of firewall rules that apply to incoming traffic:
Note that the first word in each of these examples is either “accept”, “reject”, or “drop”. This specifies the action that the firewall should do in the event that a piece of network traffic matches a rule. Accept means to allow the traffic through, reject means to block the traffic but reply with an “unreachable” error, and drop means to block the traffic and send no reply. The rest of each rule consists of the condition that each packet is matched against.
As it turns out, network traffic is matched against a list of firewall rules in a sequence, or chain, from first to last. More specifically, once a rule is matched, the associated action is applied to the network traffic in question. In our example, if an accounting employee attempted to establish an SSH connection to the server they would be rejected based on rule 2, before rule 3 is even checked. A system administrator, however, would be accepted because they would match only rule 3.
It is typical for a chain of firewall rules to not explicitly cover every possible condition. For this reason, firewall chains must always have a default policy specified, which consists only of an action (accept, reject, or drop).
Suppose the default policy for the example chain above was set to drop. If any computer outside of your office attempted to establish an SSH connection to the server, the traffic would be dropped because it does not match the conditions of any rules.
If the default policy were set to accept, anyone, except your own non-technical employees, would be able to establish a connection to any open service on your server. This would be an example of a very poorly configured firewall because it only keeps a subset of your employees out.
As network traffic, from the perspective of a server, can be either incoming or outgoing, a firewall maintains a distinct set of rules for either case. Traffic that originates elsewhere, incoming traffic, is treated differently than outgoing traffic that the server sends. It is typical for a server to allow most outgoing traffic because the server is usually, to itself, trustworthy. Still, the outgoing rule set can be used to prevent unwanted communication in the case that a server is compromised by an attacker or a malicious executable.
In order to maximize the security benefits of a firewall, you should identify all of the ways you want other systems to interact with your server, create rules that explicitly allow them, then drop all other traffic. Keep in mind that the appropriate outgoing rules must be in place so that a server will allow itself to send outgoing acknowledgements to any appropriate incoming connections. Also, as a server typically needs to initiate its own outgoing traffic for various reasons—for example, downloading updates or connecting to a database—it is important to include those cases in your outgoing rule set as well.
Suppose our example firewall is set to drop outgoing traffic by default. This means our incoming accept rules would be useless without complementary outgoing rules.
To complement the example incoming firewall rules (1 and 3), from the Firewall Rules section, and allow proper communication on those addresses and ports to occur, we could use these outgoing firewall rules:
Note that we don’t need to explicitly write a rule for incoming traffic that is dropped (incoming rule 2) because the server doesn’t need to establish or acknowledge that connection.
Now that we’ve gone over how firewalls work, let’s take a look at common software packages that can help us set up an effective firewall. While there are many other firewall-related packages, these are effective and are the ones you will encounter the most.
Iptables is a standard firewall included in most Linux distributions by default (a modern variant called nftables will begin to replace it). It is actually a front end to the kernel-level netfilter hooks that can manipulate the Linux network stack. It works by matching each packet that crosses the networking interface against a set of rules to decide what to do.
To learn how to implement a firewall with iptables, check out these links:
UFW, which stands for Uncomplicated Firewall, is an interface to iptables that is geared towards simplifying the process of configuring a firewall.
To learn more about using UFW, check out this tutorial: How To Setup a Firewall with UFW on an Ubuntu and Debian Cloud Server.
FirewallD is a complete firewall solution available by default on CentOS 7 servers. Incidentally, FirewallD uses iptables to configure netfilter.
To learn more about using FirewallD, check out this tutorial: How To Configure FirewallD to Protect Your CentOS 7 Server.
If you’re running CentOS 7 but prefer to use iptables, follow this tutorial: How To Migrate from FirewallD to Iptables on CentOS 7.
Fail2ban is an intrusion prevention software that can automatically configure your firewall to block brute force login attempts and DDOS attacks.
To learn more about Fail2ban, check out these links:
Now that you understand how firewalls work, you should look into implementing a firewall that will improve your security of your server setup by using the tutorials above.
A firewall is a software program or piece of hardware that helps screen out hackers, viruses, and worms that try to reach your computer over the Internet. If you can’t start Windows Firewall or you are getting an error, use Microsoft free tool to diagnose and fix problems.
A firewall is a network security device located between your internal network and the wider Internet. A firewall monitors incoming and outgoing network traffic – blocking or allowing it based on a set of configurable rules.
Firewalls are a fundamental piece of security and typically form the first line of defence on a network. Acting as a filter against bad connections from the outside world.
A firewall works by comparing the data sent into or out of the network against a list of rules. Based on the results of the rule checking, the firewall will then either block or allow the connection.
Firewalls work by inspecting data packets (small chunks of data) against an internal list of rules. Here are some of the more common ones:
A firewall scans the contents of the packet and then determines whether to let it through based on the rules in place. On a typical network setup, all connections to the Internet flow through the firewall. Meaning it inspects all inbound or outgoing packets.
The process of inspection involves comparing a packet’s contents against the firewall’s set of rules. Depending on if the rule is setup as a blacklist or whitelist, it will react differently to a match.
A firewall’s rules are highly configurable. Meaning you can make the packet inspection process unique to your security setup. Here are some examples of how you could use custom firewall rules:
Firewalls are often compared to a lock on the door to your network. But it might be more accurate to say that a firewall is the door.
Without a firewall in place, any connection can flow freely in or out of your network. Including connections from known malicious sources. This means you could experience unauthorised access to networked files. Leading to a data breach, malware infection or worse.
You need a firewall to filter out the bulk of malicious connections. And there’s a lot of malicious connections. One study found that within 52 seconds of being online, servers were being probed by hackers. With an average rate of 757 connection attempts per hour.
Firewalls can be either a hardware appliance or a piece of software which runs on a machine. So, the answer is both.
Not helpful, I know.
But the main difference between the two is this:
Circuit level firewalls are a type of firewall that monitors transmission control protocol (TCP) handshaking. It ensures that the communication between packets is legitimate and not malicious.
A firewall with stateful inspection considers the state of current connections when filtering packets. This means that the firewall can block the packet in one case but allowed in another. Depending on the current state of the connection.
Whilst technically not a type of firewall, UTM is instead an advanced security appliance which combines the security functions of many different security appliances. One of these being a firewall. We have an article explaining everything you need to know about UTM if you wish to learn more.
A next-generation firewall (NGFW) contains all the normal defences that a traditional firewall has and more. The most common additions are intrusion prevention software and application control. But certain vendors have other bonus security features. NGFWs are also capable of deep packet inspection which enables more robust filters.
Intrusion prevention software monitors network activity to detect and stop vulnerability exploits from occurring. This is usually done by monitoring for breaches against the network policies in place.
Application control software sets up a hard filter for programs that can send or receive data over the Internet. This can either be done by blacklist (blocks any programs in the filter) or by whitelist (blocks any programs not in the filter).
Deep Packet Inspection (DPI) is a type of packet inspection which analyses the full contents of a data packet. Instead of only information in a packet’s header (where it is coming from and going to).
This enables DPI to filter out malicious packets, such as viruses and trojans, with better accuracy. As rather than only looking at the sender and destination, the packet’s contents can be used in filters as well.
This allows DPI to uncover a broader range of security threats because it will discover packets with a malicious payload but an innocuous header.
A final piece of trivia: the name firewall originated from the real-world application of fire partitions used in buildings. These would be walls that were implemented into a building to act as a barrier to stop fire spreading from one room to another.
The similarity between a fire spreading through a building and a computer virus spreading through a network prompted the same name to be adopted for the network device.

Firewall
A firewall is a network security device located between your internal network and the wider Internet. A firewall monitors incoming and outgoing network traffic – blocking or allowing it based on a set of configurable rules.
Firewalls are a fundamental piece of security and typically form the first line of defence on a network. Acting as a filter against bad connections from the outside world.
A firewall works by comparing the data sent into or out of the network against a list of rules. Based on the results of the rule checking, the firewall will then either block or allow the connection.
Firewalls work by inspecting data packets (small chunks of data) against an internal list of rules. Here are some of the more common ones:
A firewall scans the contents of the packet and then determines whether to let it through based on the rules in place. On a typical network setup, all connections to the Internet flow through the firewall. Meaning it inspects all inbound or outgoing packets.
The process of inspection involves comparing a packet’s contents against the firewall’s set of rules. Depending on if the rule is setup as a blacklist or whitelist, it will react differently to a match.
A firewall’s rules are highly configurable. Meaning you can make the packet inspection process unique to your security setup. Here are some examples of how you could use custom firewall rules:
Firewalls are often compared to a lock on the door to your network. But it might be more accurate to say that a firewall is the door.
Without a firewall in place, any connection can flow freely in or out of your network. Including connections from known malicious sources. This means you could experience unauthorised access to networked files. Leading to a data breach, malware infection or worse.
You need a firewall to filter out the bulk of malicious connections. And there’s a lot of malicious connections. One study found that within 52 seconds of being online, servers were being probed by hackers. With an average rate of 757 connection attempts per hour.
Firewalls can be either a hardware appliance or a piece of software which runs on a machine. So, the answer is both.
Not helpful, I know.
But the main difference between the two is this:
Circuit level firewalls are a type of firewall that monitors transmission control protocol (TCP) handshaking. It ensures that the communication between packets is legitimate and not malicious.
A firewall with stateful inspection considers the state of current connections when filtering packets. This means that the firewall can block the packet in one case but allowed in another. Depending on the current state of the connection.
Whilst technically not a type of firewall, UTM is instead an advanced security appliance which combines the security functions of many different security appliances. One of these being a firewall. We have an article explaining everything you need to know about UTM if you wish to learn more.
A next-generation firewall (NGFW) contains all the normal defences that a traditional firewall has and more. The most common additions are intrusion prevention software and application control. But certain vendors have other bonus security features. NGFWs are also capable of deep packet inspection which enables more robust filters.
Intrusion prevention software monitors network activity to detect and stop vulnerability exploits from occurring. This is usually done by monitoring for breaches against the network policies in place.
Application control software sets up a hard filter for programs that can send or receive data over the Internet. This can either be done by blacklist (blocks any programs in the filter) or by whitelist (blocks any programs not in the filter).
Deep Packet Inspection (DPI) is a type of packet inspection which analyses the full contents of a data packet. Instead of only information in a packet’s header (where it is coming from and going to).
This enables DPI to filter out malicious packets, such as viruses and trojans, with better accuracy. As rather than only looking at the sender and destination, the packet’s contents can be used in filters as well.
This allows DPI to uncover a broader range of security threats because it will discover packets with a malicious payload but an innocuous header.
A final piece of trivia: the name firewall originated from the real-world application of fire partitions used in buildings. These would be walls that were implemented into a building to act as a barrier to stop fire spreading from one room to another.
The similarity between a fire spreading through a building and a computer virus spreading through a network prompted the same name to be adopted for the network device.

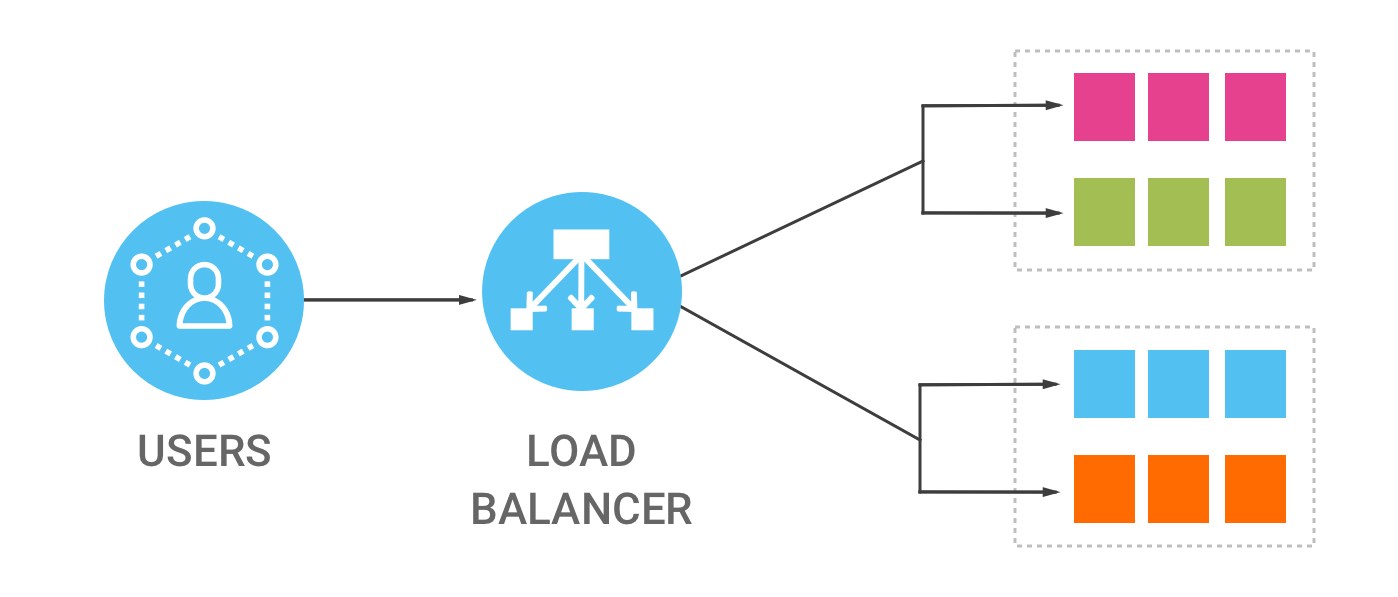
Load Balancer Provider in India
IT Monteur Provides Load Balancer, Load balancers, Load balancing, Server Load Balancer, Server Load Balancing Solutions, Array Load balancer, F5 Load Balancer, A10 Load Balancer, Load Balancing, Load Balancer, Delhi, New Delhi, Noida, Gurgaon, India
A load balancer is a device that acts as a reverse proxy and distributes network or application traffic across a number of servers. Load balancers are used to increase capacity (concurrent users) and reliability of applications.
In computing, load balancing distributes workloads across multiple computing resources, such as computers, a computer cluster, network links, central processing units or disk drives. Load balancing aims to optimize resource use, maximize throughput, minimize response time, and avoid overload of any single resource.
In computing, load balancing improves the distribution of workloads across multiple computing resources, such as computers, a computer cluster, network links, central processing units, or disk drives. Load balancing aims to optimize resource use, maximize throughput, minimize response time, and avoid overload of any single resource. Using multiple components with load balancing instead of a single component may increase reliability and availability through redundancy. Load balancing usually involves dedicated software or hardware, such as a multilayer switch or a Domain Name System server process.
Load balancing differs from channel bonding in that load balancing divides traffic between network interfaces on a network socket (OSI model layer 4) basis, while channel bonding implies a division of traffic between physical interfaces at a lower level, either per packet (OSI model Layer 3) or on a data link (OSI model Layer 2) basis with a protocol like shortest path bridging.
One of the most commonly used applications of load balancing is to provide a single Internet service from multiple servers, sometimes known as a server farm. Commonly load-balanced systems include popular web sites, large Internet Relay Chat networks, high-bandwidth File Transfer Protocol sites, Network News Transfer Protocol (NNTP) servers, Domain Name System (DNS) servers, and databases.
An alternate method of load balancing, which does not require a dedicated software or hardware node, is called round robin DNS. In this technique, multiple IP addresses are associated with a single domain name; clients are given IP in round robin fashion. IP is assigned to clients with a short expiration so the client is more likely to use a different IP the next time they access the Internet service being requested.
Another more effective technique for load-balancing using DNS is to delegate www.example.org as a sub-domain whose zone is served by each of the same servers that are serving the web site. This technique works particularly well where individual servers are spread geographically on the Internet. For example:
one.example.org A 192.0.2.1
two.example.org A 203.0.113.2
www.example.org NS one.example.org
www.example.org NS two.example.org
However, the zone file for www.example.org on each server is different such that each server resolves its own IP Address as the A-record.[2] On server one the zone file for www.example.org reports:
@ in a 192.0.2.1
On server two the same zone file contains:
@ in a 203.0.113.2
This way, when a server is down, its DNS will not respond and the web service does not receive any traffic. If the line to one server is congested, the unreliability of DNS ensures less HTTP traffic reaches that server. Furthermore, the quickest DNS response to the resolver is nearly always the one from the network’s closest server, ensuring geo-sensitive load-balancing[citation needed]. A short TTL on the A-record helps to ensure traffic is quickly diverted when a server goes down. Consideration must be given the possibility that this technique may cause individual clients to switch between individual servers in mid-session.
Another approach to load balancing is to deliver a list of server IPs to the client, and then to have client randomly select the IP from the list on each connection. This essentially relies on all clients generating similar loads, and the Law of Large Numbers[4] to achieve a reasonably flat load distribution across servers. It has been claimed that client-side random load balancing tends to provide better load distribution than round-robin DNS; this has been attributed to caching issues with round-robin DNS, that in case of large DNS caching servers, tend to skew the distribution for round-robin DNS, while client-side random selection remains unaffected regardless of DNS caching.
With this approach, the method of delivery of list of IPs to the client can vary, and may be implemented as a DNS list (delivered to all the clients without any round-robin), or via hardcoding it to the list. If a “smart client” is used, detecting that randomly selected server is down and connecting randomly again, it also provides fault tolerance.
Server-side load balancers
For Internet services, a server-side load balancer is usually a software program that is listening on the port where external clients connect to access services. The load balancer forwards requests to one of the “backend” servers, which usually replies to the load balancer. This allows the load balancer to reply to the client without the client ever knowing about the internal separation of functions. It also prevents clients from contacting back-end servers directly, which may have security benefits by hiding the structure of the internal network and preventing attacks on the kernel’s network stack or unrelated services running on other ports.
Some load balancers provide a mechanism for doing something special in the event that all backend servers are unavailable. This might include forwarding to a backup load balancer, or displaying a message regarding the outage.
It is also important that the load balancer itself does not become a single point of failure. Usually load balancers are implemented in high-availability pairs which may also replicate session persistence data if required by the specific application.[5] Scheduling algorithms
Numerous scheduling algorithms, also called load-balancing methods, are used by load balancers to determine which back-end server to send a request to. Simple algorithms include random choice, round robin, or least connections.[6] More sophisticated load balancers may take additional factors into account, such as a server’s reported load, least response times, up/down status (determined by a monitoring poll of some kind), number of active connections, geographic location, capabilities, or how much traffic it has recently been assigned.
Persistence
An important issue when operating a load-balanced service is how to handle information that must be kept across the multiple requests in a user’s session. If this information is stored locally on one backend server, then subsequent requests going to different backend servers would not be able to find it. This might be cached information that can be recomputed, in which case load-balancing a request to a different backend server just introduces a performance issue.[6]
Ideally the cluster of servers behind the load balancer should not be session-aware, so that if a client connects to any backend server at any time the user experience is unaffected. This is usually achieved with a shared database or an in-memory session database, for example Memcached.
One basic solution to the session data issue is to send all requests in a user session consistently to the same backend server. This is known as “persistence” or “stickiness”. A significant downside to this technique is its lack of automatic failover: if a backend server goes down, its per-session information becomes inaccessible, and any sessions depending on it are lost. The same problem is usually relevant to central database servers; even if web servers are “stateless” and not “sticky”, the central database is (see below).
Assignment to a particular server might be based on a username, client IP address, or be random. Because of changes of the client’s perceived address resulting from DHCP, network address translation, and web proxies this method may be unreliable. Random assignments must be remembered by the load balancer, which creates a burden on storage. If the load balancer is replaced or fails, this information may be lost, and assignments may need to be deleted after a timeout period or during periods of high load to avoid exceeding the space available for the assignment table. The random assignment method also requires that clients maintain some state, which can be a problem, for example when a web browser has disabled storage of cookies. Sophisticated load balancers use multiple persistence techniques to avoid some of the shortcomings of any one method.
Another solution is to keep the per-session data in a database. Generally this is bad for performance because it increases the load on the database: the database is best used to store information less transient than per-session data. To prevent a database from becoming a single point of failure, and to improve scalability, the database is often replicated across multiple machines, and load balancing is used to spread the query load across those replicas. Microsoft’s ASP.net State Server technology is an example of a session database. All servers in a web farm store their session data on State Server and any server in the farm can retrieve the data.
In the very common case where the client is a web browser, a simple but efficient approach is to store the per-session data in the browser itself. One way to achieve this is to use a browser cookie, suitably time-stamped and encrypted. Another is URL rewriting. Storing session data on the client is generally the preferred solution: then the load balancer is free to pick any backend server to handle a request. However, this method of state-data handling is poorly suited to some complex business logic scenarios, where session state payload is big and recomputing it with every request on a server is not feasible. URL rewriting has major security issues, because the end-user can easily alter the submitted URL and thus change session streams.
Yet another solution to storing persistent data is to associate a name with each block of data, and use a distributed hash table to pseudo-randomly assign that name to one of the available servers, and then store that block of data in the assigned server.
Hardware and software load balancers may have a variety of special features. The fundamental feature of a load balancer is to be able to distribute incoming requests over a number of backend servers in the cluster according to a scheduling algorithm. Most of the following features are vendor specific:
A ratio can be manually assigned to cause some backend servers to get a greater share of the workload than others. This is sometimes used as a crude way to account for some servers having more capacity than others and may not always work as desired.
Priority activation
When the number of available servers drops below a certain number, or load gets too high, standby servers can be brought online.
TLS (or its predecessor SSL) acceleration is a technique of offloading cryptographic protocol calculations onto a specialized hardware. Depending on the workload, processing the encryption and authentication requirements of an TLS request can become a major part of the demand on the Web Server’s CPU; as the demand increases, users will see slower response times, as the TLS overhead is distributed among Web servers. To remove this demand on Web servers, a balancer can terminate TLS connections, passing HTTPS requests as HTTP requests to the Web servers. If the balancer itself is not overloaded, this does not noticeably degrade the performance perceived by end users. The downside of this approach is that all of the TLS processing is concentrated on a single device (the balancer) which can become a new bottleneck. Some load balancer appliances include specialized hardware to process TLS. Instead of upgrading the load balancer, which is quite expensive dedicated hardware, it may be cheaper to forgo TLS offload and add a few Web servers. Also, some server vendors such as Oracle/Sun now incorporate cryptographic acceleration hardware into their CPUs such as the T2000. F5 Networks incorporates a dedicated TLS acceleration hardware card in their local traffic manager (LTM) which is used for encrypting and decrypting TLS traffic. One clear benefit to TLS offloading in the balancer is that it enables it to do balancing or content switching based on data in the HTTPS request.
Load balancers can provide features such as SYN cookies and delayed-binding (the back-end servers don’t see the client until it finishes its TCP handshake) to mitigate SYN flood attacks and generally offload work from the servers to a more efficient platform.
HTTP compression reduces the amount of data to be transferred for HTTP objects by utilising gzip compression available in all modern web browsers. The larger the response and the further away the client is, the more this feature can improve response times. The trade-off is that this feature puts additional CPU demand on the load balancer and could be done by web servers instead.
Different vendors use different terms for this, but the idea is that normally each HTTP request from each client is a different TCP connection. This feature utilises HTTP/1.1 to consolidate multiple HTTP requests from multiple clients into a single TCP socket to the back-end servers.
The load balancer can buffer responses from the server and spoon-feed the data out to slow clients, allowing the web server to free a thread for other tasks faster than it would if it had to send the entire request to the client directly.
An option for asymmetrical load distribution, where request and reply have different network paths.
The balancer polls servers for application layer health and removes failed servers from the pool.
The balancer stores static content so that some requests can be handled without contacting the servers.
Some balancers can arbitrarily modify traffic on the way through.
Some balancers can hide HTTP error pages, remove server identification headers from HTTP responses, and encrypt cookies so that end users cannot manipulate them.
Also known as rate shaping, the ability to give different priority to different traffic.
Most load balancers can send requests to different servers based on the URL being requested, assuming the request is not encrypted (HTTP) or if it is encrypted (via HTTPS) that the HTTPS request is terminated (decrypted) at the load balancer.
Authenticate users against a variety of authentication sources before allowing them access to a website.
At least one balancer allows the use of a scripting language to allow custom balancing methods, arbitrary traffic manipulations, and more.
Firewalls can prevent direct connections to backend servers, for network security reasons.
Intrusion prevention systems offer application layer security in addition to network/transport layer offered by firewall security.
Load balancing can be useful in applications with redundant communications links. For example, a company may have multiple Internet connections ensuring network access if one of the connections fails. A failover arrangement would mean that one link is designated for normal use, while the second link is used only if the primary link fails.
Using load balancing, both links can be in use all the time. A device or program monitors the availability of all links and selects the path for sending packets. The use of multiple links simultaneously increases the available bandwidth.
The IEEE approved the IEEE 802.1aq standard May 2012, also known and documented in most books as Shortest Path Bridging (SPB). SPB allows all links to be active through multiple equal cost paths, provides faster convergence times to reduce down time, and simplifies the use of load balancing in mesh network topologies (partially connected and/or fully connected) by allowing traffic to load share across all paths of a network.[8][9] SPB is designed to virtually eliminate human error during configuration and preserves the plug-and-play nature that established Ethernet as the de facto protocol at Layer 2.
Many telecommunications companies have multiple routes through their networks or to external networks. They use sophisticated load balancing to shift traffic from one path to another to avoid network congestion on any particular link, and sometimes to minimize the cost of transit across external networks or improve network reliability.
Another way of using load balancing is in network monitoring activities. Load balancers can be used to split huge data flows into several sub-flows and use several network analyzers, each reading a part of the original data. This is very useful for monitoring fast networks like 10GbE or STM64, where complex processing of the data may not be possible at wire speed.
Load balancing is widely used in data center networks to distribute traffic across many existing paths between any two servers.[12] It allows more efficient use of network bandwidth and reduces provisioning costs. In general, load balancing in datacenter networks can be classified as either static or dynamic. Static load balancing distributes traffic by computing a hash of the source and destination addresses and port numbers of traffic flows and using it to determine how flows are assigned to one of the existing paths. Dynamic load balancing assigns traffic flows to paths by monitoring bandwidth utilization of different paths. Dynamic assignment can also be proactive or reactive. In the former case, the assignment is fixed once made, while in the latter the network logic keeps monitoring available paths and shifts flows across them as network utilization changes (with arrival of new flows or completion of existing ones). A comprehensive overview of load balancing in datacenter networks has been made available.
Load balancing is often used to implement failover—the continuation of a service after the failure of one or more of its components. The components are monitored continually (e.g., web servers may be monitored by fetching known pages), and when one becomes non-responsive, the load balancer is informed and no longer sends traffic to it. When a component comes back online, the load balancer begins to route traffic to it again. For this to work, there must be at least one component in excess of the service’s capacity (N+1 redundancy). This can be much less expensive and more flexible than failover approaches where each single live component is paired with a single backup component that takes over in the event of a failure (dual modular redundancy). Some types of RAID systems can also utilize hot spare for a similar effect.
Load balancing refers to spreading a service load among multiple server systems. A hardware load balancer or software-based load balancing tool can ensure maximum service availability by offering network traffic distribution services.
For example, if your business has a primary business domain (e.g., www.yourbusiness.com), you want your site available to your current customers and your potential customers 100 percent of the time. Comparing the top server load balancers (SLBs) and effectively utilizing their load-balancing capabilities will help provide this level of availability.
When technical folks discuss load balancing, they generally mean hardware load balancer devices dedicated to the task of balancing network traffic loads. A hardware load balancer is a server computer with a very specialized operating system tuned to manage network traffic using user-created rules.
While these hardware load balancer devices have since evolved into what are now called application delivery controllers (ADC), load balancing remains at the heart of an ADC. Enterprises and hosting companies rely on load-balancing and ADC devices to distribute traffic to create highly available services.
In addition to providing simple distributed service to multiple servers, load balancers can help prevent denial-of-service attacks, allow legitimate users uninterrupted access to services, protect against single point of failure outages and prevent traffic bottlenecks to systems.
Today we’ll highlight a handful of the leading hardware load balancers as well as several cloud and software-based load balancer options.
A10 Networks
Avi Networks
aiScaler
Akamai Technologies
Alcatel-Lucent (Enterprise)
Array Networks
Aryaka
Barracuda Networks
Blue Coat Systems
Brocade Communications
CDNetworks
Citrix
Cisco Systems
Cotendo
Crescendo Networks
EdgeCast Networks
Exinda
Expand Networks
F5 Networks
Fortinet
Foundry Networks
Instart Logic
Internap
Ipanema Technologies
Juniper Networks
KEMP Technologies
Limelight Networks
Netlify
Nortel
Radware
Riverbed Technology
Streamcore
Sun Microsystems
Zeus Technology
Please call on
![]()
Buy Fortinet – FortiGate Firewalls Online Price
Fortinet – FortiGate Firewall |
Price |
| FortiGate-30E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 1 to 15 users |
Rs.53,395/- |
| FortiGate-60E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 1 to 40 users |
Rs. 72,331/- |
| FortiGate-80E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 1 to 40 users |
Rs. 88,902/- |
| FortiGate-90E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 15 to 60 users |
Rs. 1,20,438/- |
| FortiGate-100E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 15 to 100 users |
Rs. 1,74,757/- |
![]()
Buy Sophos Firewall Online Price
Sophos Firewall |
Price |
| Sophos XG 85 with Full Guard 1 year license ( For 20 User ) |
Rs. 28,078 |
| Sophos XG 105 with Full Guard 1 year license ( For 30 User ) |
Rs. 42,237.65 |
| Sophos XG 115 with Full Guard 1 year license ( For 50 User ) |
Rs. 68,914.30 |
| Sophos XG 125 with Full Guard 1 year license ( For 70 User ) |
Rs. 98,508.00 |
| Sophos XG 135 with Full Guard 1 year license ( For 100 User ) |
Rs. 159,432.00 |
![]()
Buy WatchGuard Firewall Online Price
Watch Guard Firewall |
Price |
| WatchGuard Firewall Firebox T15 with 1-Year Total Security Suite ( For 10 User ) |
Rs. 43,520/- |
| WatchGuard Firewall Firebox T35 with 1-Year Total Security Suite ( For 30 User ) |
Rs. 86,020/- |
| WatchGuard Firewall Firebox T70 with 1-Year Total Security Suite ( For 50 User ) |
Rs. 1,36,000/- |
| WatchGuard Firewall Firebox M270 with 1-Year Total Security Suite ( For 100 User ) |
Rs. 2,81,220/- |
| WatchGuard Firewall Firebox M370 with 1-Year Total Security Suite ( For 150 User ) |
Rs. 3,58,060/- |
Sale! 
Showing all 1 result

Firewall Network Security Solutions Provider in Dubai UAE
40% of all cyber-attacks target businesses with fewer than 500 employees!
More than 40% of SMBs don’t have an adequate IT security budget!
SMBs on average lose $188,242 to a cyber attack and almost 66% of victimized companies are forced out of business within six months of being attacked.
Only 26% of small and midsize businesses were confident their firm has enough in-house expertise for a strong security posture
Despite the threat that data loss poses to SMBs, 70% thought their companies would have difficulty detecting a breach
Did you know the average breach goes undetected for 229 days?
Regardless of the size of your business, you want to be assured of the security of your computers and networks. IT Monteur Firewall Firm team can ensure your business has around the clock firewall and virus protection, guaranteeing your network is free from intrusion, spyware and hackers 24/7.
Many small business owners feel safe from attack, mistakenly thinking hackers only target large corporations. The fact is that many cyber criminals see smaller businesses as ideal targets due to their minimal security measures, and often use those smaller businesses to gain access to the networks of larger companies.
Security at all levels of I.T. is vital to ensure you aren’t seen as an easy target. It isn’t something you want to address once your systems have been compromised. IT Monteur Firewall Firm can assist, with integrated firewalls, network and desktop security solutions, virus protection, spam filtering, adware, spyware protection and much more.
When any enterprise or small medium business start thinking of a network management & security, the first thing to come up in the mind of IT Managers is a good and secure firewall. Firewalls are the first layer of defense in a network, as a system without the basic layer of security is intended to reveal the sensitive data for enterprise users.
A firewall is a combo of a firewall software and operating system that is built to run a firewall system on a dedicated hardware or virtual machine which includes :
Security solutions at IT Monteur is aimed to protect your business from hackers attack and other Internet threats. We aim at running your business smooth without any worry about securing your data. IT Monteur a Firewall Company in Dubai UAE, provides firewall software and hardware firewall to protect your data from any mallacious attacks and unexpected crises.
Firewall Software and Hardware Firewall solutions are both designed to block unauthorized access to computers in your network. A firewall software program is installed on each individual PC it’s meant to protect. To safeguard all your company’s computers, however, each one must have a software firewall installed. This can become expensive and difficult to maintain and support. But, a hardware-based firewall is easier to maintain and administer than individual software firewalls. It protect all the computers on your network.
Our firewall security solutions is Combined network and physical security for a more comprehensive approach that meets your needs and that allows you to add integrated protection from hackers, spam, malicious websites, identity theft.
we provide secure access to enable workers at home, at remote sites, or traveling to connect to your business safely and securely Secure storage that gives you the flexible capacity to protect and back up data, video, and images and also provide Physical protection to guard your business and your employees from theft, vandalism, and unlawful access.
Our firewall security solutions Key features:
We are also providing UTM ( Unified threat management ) Firewall Solutions for SMB & Enterprices
Firewalls, both hardware and software, protect computers from hackers and other online threats by blocking dangerous pieces of data from reaching the system. While hardware firewalls offer network-wide protection from external threats, software firewalls installed on individual computers can more closely inspect data, and can block specific programs from even sending data to the Internet. On networks with high security concerns, combining both kinds of firewalls provides a more complete safety net.
We are providing UTM ( Unified threat management ) Best Firewall Solutions for SMB & Enterprises Companies in Dubai UAE

Firewall India
Protecting your network from intruders is as essential as locking up the front door. If the firewall architecture is poorly set up, or non-existent, it might have a significant impact on your business IT security. If an intruder penetrates your network it could lead to sensitive data being stolen, financial loss, or worse.
Servicing in Delhi NCR India, we can provide support and help your business implement the following firewalls:
With almost 15 years’ experience within the IT industry, Solutions Plus is proud to be a reseller of all firewall solutions in Delhi NCR India. With our partnership, we supply and support all firewall products, as well as Wireless Access Points and Email Gateways. We truly believe that they are the best on the market.
Learn more about our partnership with all firewall company or for more information on our firewall management services, please call us on Sales :+91 958 290 7788 | Support : +91 94 8585 7788
When any enterprise or small medium business start thinking of a network management & security, the first thing to come up in the mind of IT Managers is a good and secure firewall. Firewalls are the first layer of defense in a network, as a system without the basic layer of security is intended to reveal the sensitive data for enterprise users.
A firewall is a combo of a firewall software and operating system that is built to run a firewall system on a dedicated hardware or virtual machine which includes :

Firewall India
| Firewall | License | Cost | OS |
|---|---|---|---|

Check Point |
Proprietary | Included on Check Point security gateways |
Proprietary operating system Check Point IPSO and Gaia (Linux-based) |

FortiGate |
Proprietary | Included on all Fortigate devices |
Proprietary, FortiOS |

Palo Alto Networks |
Proprietary | Included on Palo Alto Networks firewalls |
Proprietary operating system PANOS |

WatchGuard |
Proprietary | Included on all WatchGuard firewalls |
Proprietary operating system |

Sophos |
Proprietary | Included on Sophos UTM | Linux-based appliance |

Cisco Asa Firepower |
Proprietary | Included on all CISCO ASA devices |
Proprietary operating system |

Cisco PIX |
Proprietary | Included on all CISCO PIX devices |
Proprietary operating system |

Forcepoint |
Proprietary | Included on Intel Security Appliance | Linux-based appliance |

Juniper SSG |
Proprietary | Included on Netscreen security gateways |
Proprietary operating system ScreenOS |

Juniper SRX |
Proprietary | Included on SRX security gateways |
Proprietary operating system Junos |

Sonicwall |
Proprietary | Included on Dell appliance | Proprietary operating system SonicOs |

Barracuda Firewall |
Proprietary | Included Firewall Next Generation appliance | Windows-based appliance embedded firewall distribution |

Cyberoam |
Proprietary | Included Firewall Sophos appliance | Windows-based appliance embedded firewall distribution |
| D-Link | Proprietary | Included Firewall DFL | Windows-based appliance embedded firewall distribution |
| Endian Firewall | Proprietary | Free / Paid | Linux-based appliance |
| Opendium Iceni | Proprietary | Free / Paid | Linux-based, with optional web filtering / auditing. |
| IPCop | GPL | Free / Paid | Linux-based appliance firewall distribution |
|
pfSense |
ESF/BSD | Free / Paid | FreeBSD-based appliance firewall distribution |
| IPFire | GPL | Free / Paid | Linux/NanoBSD-based appliance firewall distribution |
| Untangle | GPL | Free / Paid | Linux/NanoBSD-based appliance firewall distribution |
| Zeroshell | GPL | Free / Paid | Linux/NanoBSD-based appliance firewall distribution |
| SmoothWall | GPL | Free / Paid | Linux-based appliance embedded firewall distribution |
| WinGate | GPL | Free / Paid | Windows-based appliance embedded firewall distribution |
| Calyptix Security | BSD | Free | OpenBSD-based appliance firewall distribution |
| Halon Security | BSD | Free | OpenBSD-based appliance |
| Vantronix | BSD | Free | OpenBSD-based appliance |

Firewall India


Fortinet – Fortigate Firewall Providers in India
Firewall Firm is a Fortigate Firewall Provider in India, Fortinet Consolidated Security Platform delivers unmatched performance and protection while simplifying your network. Fortinet’s Network Security Appliances offer models to satisfy any deployment requirement from the FortiGate-20 series for Small Offices to the FortiGate-5000 series for very Large Enterprises, Service Providers and Carriers. FortiGate platforms integrate the FortiOS operating system with FortiASIC processors and the latest-generation CPUs to provide comprehensive.
Buy Hardware Appliance UTM Firewall from Firewall Firm Fortigate Firewall Provider in India, is authorized Dealer, Partner, Supplier, Reseller with remote, on-site installation support in India at best price.
We are Providing our Antivirus, Antispam solutions all over India like Mumbai, Thane, Navi Mumbai, Vasai. Virar, Panvel, Kharghar, Bhiwandi, Kalyan Gujrat, Kolkata, Dehli, Chennai, Tamil Nadu etc. To buy our Firewall Service contact us.
FortiGate® Network Security Platform
High-End
Mid-Range
Desktops
Application Firewall
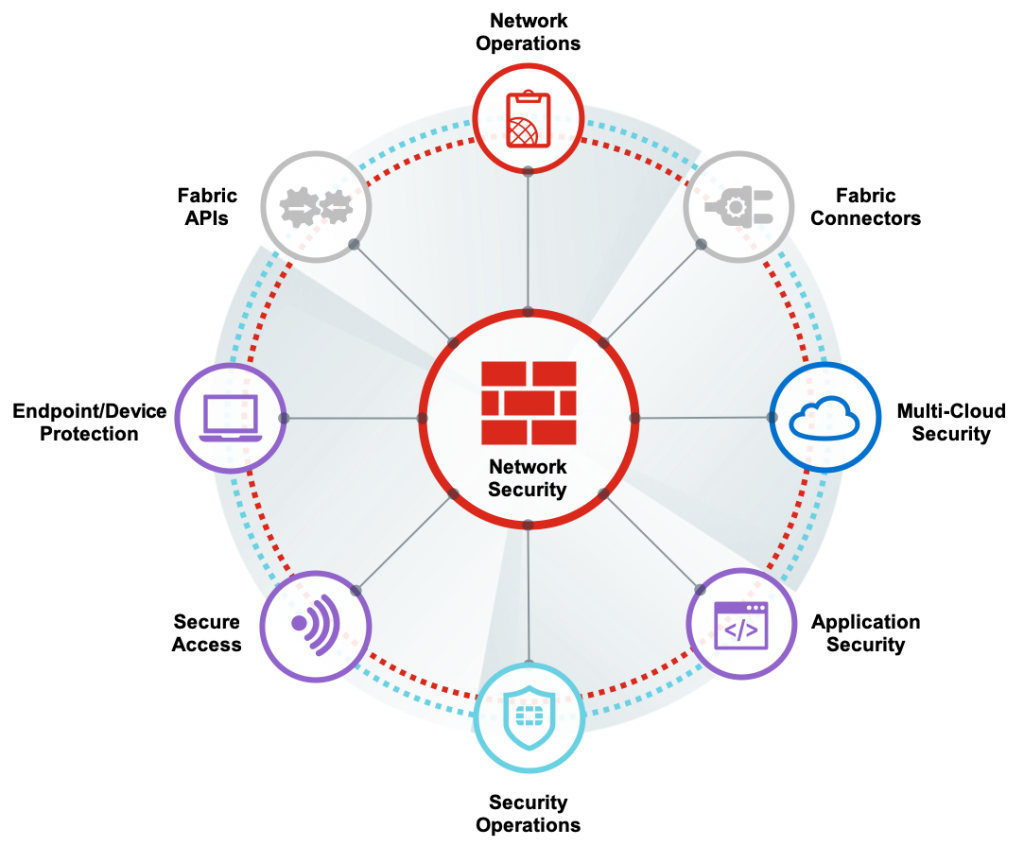
Network Security
Network Security Fortinet’s high-performance FortiGate firewalls—powered by our purpose-built OS, security processors, and threat intelligence from FortiGuard Labs—provide consolidated, advanced security and deep visibility that protects the network from known and unknown threats.
Fortinet’s Solution for the Enterprise Campus
Connected UTM Solution Brief
Application Delivery Network Solutions From Fortinet
Fortinet Data Center Solution Brief
Fortinet UTM Solution Guide
The Password as you Know it is Dead
Fortinet Secure Wireless LAN
IT Monteur understands the increasing threats faced by the SME community, and can offer the right solutions tailored to your company’s needs.
To support employee mobility, many small offices are adding wireless and enabling BYOD – technologies that have traditionally been confined to larger enterprises. These new technologies add new data security and compliance requirements.
Small businesses have historically lacked security capabilities often found at larger enterprises, primarily due to cost and complexity. For this reason, data breaches are increasingly hitting smaller organisations, either for their data or access to the larger businesses they may serve.
According to the Verizon Data Breach Incident Report, data breaches were more common in small than large organisations (25% vs 20%, with 50% from size unknown).
Fortinet’s commitment to quantified, independent third party validation of security effectiveness is unmatched in the industry. Security technologies deployed from network edge to individual endpoints have all earned top marks in real-world testing by NSS Labs, Virus Bulletin, AV Comparatives and more.
Fortinet is the only UTM vendor able to offer the broad range of security and networking capabilities to dramatically simplify IT infrastructure and security.
Because all products are built in-house they will integrate more tightly and reduce your administration. Your life becomes even easier by working with a single vendor, single procurement process, single administrative experience across products, single support group and single volume licensing program.
Form Factor – Expandable, modular chassis
Interfaces – 10, 40, and 100 GE
FW(TP) Throughput – More than 1 Tbps (Up to 189 Gbps)
Special Features – Carrier class, NEBS, fully redundant
Form Factor – 2RU – 5RU appliance
Interfaces10, 25, 40, and 100 GE
FW(TP) Throughput – 52 Gbps – 1 Tbps (4 Gbps – 100 Gbps)
Special Features Ultra-low latency, ultra high-speed SSL inspection
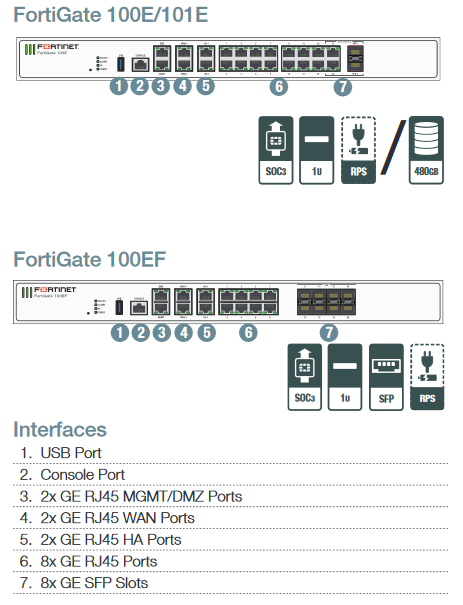
Form Factor – 1RU – 2RU appliance
Interfaces1 and 10 GE
FW(TP) Throughput – 7 Gbps – 36 Gbps (1 Gbps – 7 Gbps)
Special Features High-speed SSL inspection
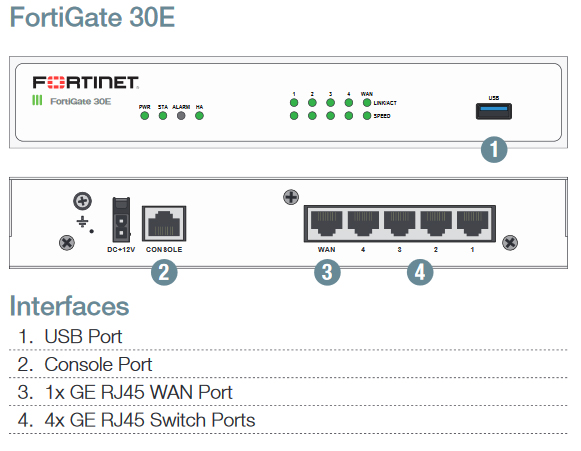 Form Factor – Desktop
Form Factor – Desktop
Interfaces – High-density 1 GE
FW(TP) Throughput1 – 4 Gbps (150 Mbps – 250 Mbps)
Special Features – Wi-Fi, PoE, ruggedized
Private Cloud
Use Cases &Integrations – All major hypervisors VMware NSX, Cisco ACI, OpenStack, Nuage, Azure Stack
Throughput – Hardware dependent
Licensing – Perpetual, subscription, metered
Public Cloud
Use Cases &Integrations – AWS, Azure, Google, Oracle,IBM, Alibaba
Throughput – Cloud dependent
Licensing – BYOL or on-demand
| Fortinet – FortiGate Firewall | Price |
| FortiGate-30E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 1 to 15 users |
Rs.53,395/- |
| FortiGate-60E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 1 to 40 users |
Rs. 72,331/- |
| FortiGate-80E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 1 to 40 users |
Rs. 88,902/- |
| FortiGate-90E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 15 to 60 users |
Rs. 1,20,438/- |
| FortiGate-100E Hardware plus 1 year 8×5 Forticare and FortiGuard UTM Bundle 15 to 100 users |
Rs. 1,74,757/- |
Our web application firewall – Website Firewall is designed to filter traffic before it reaches your WordPress or Joomla website. The majority of malicious website attacks are therefore blocked which increases website security dramatically.
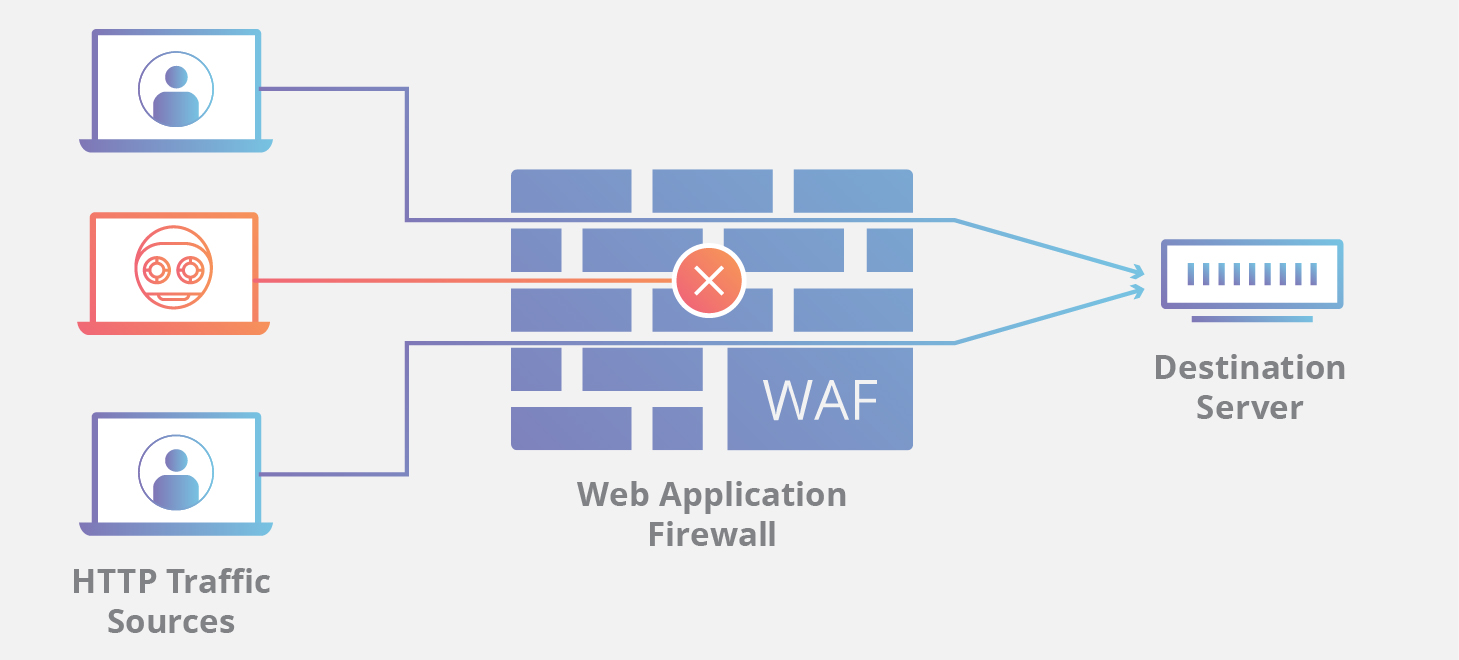
Website Firewall
Traditional firewalls protect IT environments against external attacks, by allowing and blocking connections to certain areas.
These firewalls control incoming and outgoing network traffic, based on a set of rules.
Here is a basic example:
Let’s suppose your company has a web server inside its infrastructure. In order for the web server to be reachable from outside your company, some rules will have to be established to authorize web traffic to and from that server.
Some “ports” will be open, on a given IP address (the one of your server).
Your company can choose to allow web traffic only, or allow other traffic according to its needs.
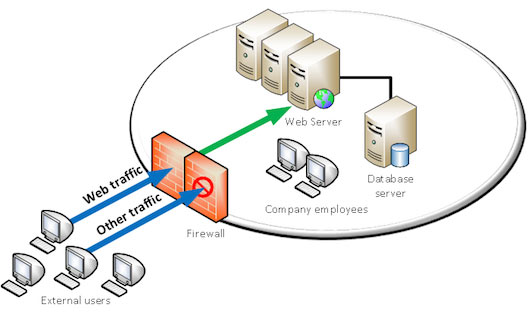
Traditional Firewall – web traffic enabled
In our example, allowing web traffic only does not guarantee that this traffic is safe.
The web has enabled many possibilities and allowed easy access to resources and data. Unfortunately, web technologies are not completely safe by nature and threats are as numerous as opportunities. Traditional firewalls cannot analyze in details what is reaching the server.
By opening communication channels to web servers, the door is also open to new threats: application attacks.
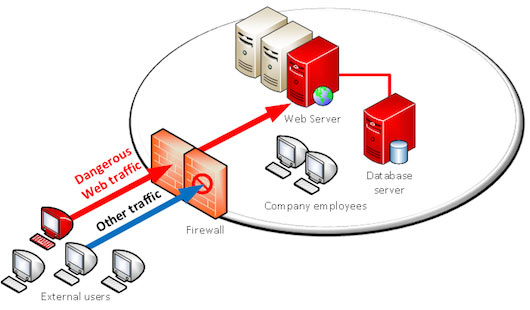
Traditional Firewall – dangerous traffic coming in
The web traffic can embed many types of attacks: SQL injections, Cross Site Scripting, Cross Site Request Forgery, session hijacking attacks… hundreds of possible attacks.
This is where web application firewalls (WAF) have their role to play.
By analyzing web traffic, and with a smart detection engine, web application firewalls are able to distinguish dangerous from legitimate traffic and block attacks.
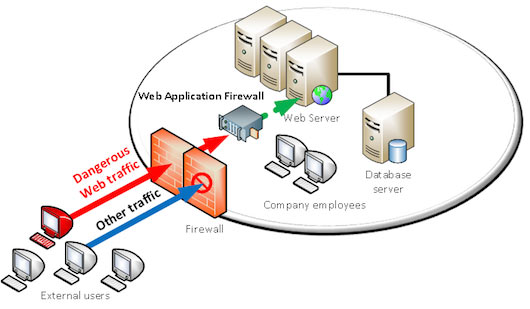
Web Application Firewall blocking dangerous traffic
From a technical standpoint and referring to the OSI model (conceptual model describing communication system layers), traditional firewalls act on the three first layers (physical to network layers), and web application firewalls act on the seventh layer (application layer).
Get website protection and performance with a professional team to help.
The Website Firewall is a cloud-based WAF that stops website hacks and attacks. Our constant research improves our detection and mitigation of evolving threats, and you can add your own custom rules.
Our CDN makes your site faster and highly available across the world. Built on our global network of secure data centers, your visitors, customers, and search engines will notice a dramatic improvement.
Website Firewall is a managed security solution for websites. Our cloud-based platform gives you complete website security, including an antivirus and firewall for your website.
We monitor for security incidents, fix website hacks, and protect your site to keep hackers out. The platform also keeps your website running fast and ensures operational continuity.
Any website owner or business that wants to stop worrying about website security and have it managed on their behalf by trusted and experienced professionals.
Website owners and server administrators who prefer to develop and implement their own DIY approach to website protection, monitoring, and remediation.
We extensively research website hacks and build security tools that respond to a constantly evolving world of cyber threats.
It doesn’t matter how your website was built. Whether it has a CMS or custom code, your web server and database is safe with us.
No complicated configuration or installation. You can set it and forget it, or customize freely. We are here to help you at every step.
You can scan your site for free with our website security scanner, SiteCheck. Remote scanners are limited to detecting payloads visible in your website source code. If you need help with incident response and more thorough detection, try the full Website Firewall Security Platform.
| Basic | Pro | Business | |
| Price (Per Site) |
$349.99/yr |
$499.99/yr |
$599.99/yr |
| Malware & Hack Scan Frequency |
12 hrs |
6 hrs |
30 mins |
| Malware Removal & Hack Cleanup | |||
| Brand Reputation & Blacklist Monitoring | |||
| Stop Hacks (Virtual Patching / Hardening) | |||
| Advanced DDoS Mitigation | |||
| CDN Performance | |||
| SSL Certificate Support | |||
| Firewall – SSL & PCI Compliant | |||
| Customer Support | |||
for more details, please contact us on

Made_in_India
When any enterprise or small medium business start thinking of a network management & security, the first thing to come up in the mind of IT Managers is a good and secure firewall. Firewalls are the first layer of defense in a network, as a system without the basic layer of security is intended to reveal the sensitive data for enterprise users.
A firewall is a combo of a firewall software and operating system that is built to run a firewall system on a dedicated hardware or virtual machine which includes :
Embedded firewalls: very limited-capability programs running on a low-power CPU system,
Software firewall appliances: a system that can be run in independent hardware or in a virtualised environment as a virtual appliance
Hardware firewall appliances: Hardware firewall is specifically built to install as a network device, providing enough network interfaces and CPU to serve a wide range of purposes. From protecting a small network to protecting an enterprise-level network.
Vendors and Products of Indian Firewall Manufacturer
|
|
|
Dwarpal |
||
Seqrite |
||
GajShield |
 Made_in_India |
 |
Prime Minister Narendra Modi has launched his big “Make in India” campaign, with the aim of turning the India into a global hub of manufacturing, with His Initiative of Digital India, Make in India, Many IT Companies started doing manufacture of Security Firewalls.

Made-in-India
What is Firewall? A Firewall is a network security device that monitors and filters incoming and outgoing network traffic based on an organization's previously established security policies. At its most basic, a firewall is essentially the barrier that sits between a private internal network and the public Internet.
Secure your network at the gateway against threats such as intrusions, Viruses, Spyware, Worms, Trojans, Adware, Keyloggers, Malicious Mobile Code (MMC), and other dangerous applications for total protection in a convenient, affordable subscription-based service. Modern threats like web-based malware attacks, targeted attacks, application-layer attacks, and more have had a significantly negative effect on the threat landscape. In fact, more than 80% of all new malware and intrusion attempts are exploiting weaknesses in applications, as opposed to weaknesses in networking components and services. Stateful firewalls with simple packet filtering capabilities were efficient blocking unwanted applications as most applications met the port-protocol expectations. Administrators could promptly prevent an unsafe application from being accessed by users by blocking the associated ports and protocols.
Firewall Firm is an IT Monteur Firewall Company provides Managed Firewall Support, Firewall providers , Firewall Security Service Provider, Network Security Services, Firewall Solutions India , New Delhi - India's capital territory , Mumbai - Bombay , Kolkata - Calcutta , Chennai - Madras , Bangaluru - Bangalore , Bhubaneswar, Ahmedabad, Hyderabad, Pune, Surat, Jaipur, Firewall Service Providers in India
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India