Evidence shows CISO is being wrongly implicated, ET CISO
Star Health Insurance did suffer a data breach incident – a massive one, in fact, there’s no refuting that. However, allegations made by the threat actor implicating the company’s CISO, Amarjeet Khanuja, are rife with inconsistencies and anyone with a slim understanding of how enterprise security works can spot holes in the story.
A cyber criminal lying? You don’t say.
ETCISO spoke with security researchers and CISOs who have observed and analyzed the incident closely. In this story, we aim to bring to light what really transpired and the glaring irregularities in the adversary’s narrative.
The other question we intend to address is how 7 TB of data comprising highly sensitive information could be stolen without being detected. CISOs also tell us essential security measures security leaders must follow to avoid insider compromise and massive data exfiltration.
The Data Breach
The threat actor who goes by the name Xenzen claims to have purchased 7.24 TB of data comprising sensitive information such as full names, addresses, PAN numbers, mobile numbers, email addresses, policy details, and health-related information such as height, weight, and pre-existing diseases.
The leak of health-related information is what makes this breach incident concerning as data is unchangeable and permanent. Furthermore, pre-existing health conditions of individuals can be misused by adversaries.
The stolen data was hosted on two Telegram channels: StarHealthLeak_CustomerData_Bot and StarHealthLeak_ClaimsData_Bot.
Notably, Xenzen was also involved in the purported July 2024 Airtel data breach incident. A month before that, the threat actor allegedly leaked the Ministry of External Affairs’ database for blue-collar workers on Breach Forum – a marketplace for stolen or leaked databases.
What the Threat Actor Claims
Rakesh Krishnan, Senior Threat Analyst at Netenrich and an independent security researcher spoke with ETCISO and shared evidence of the data breach incident, email correspondence with the threat actor and their allegations.
The threat actor says on Leak Source: “Star Health management CISO Amarjeet sold all this data to me and then attempted to change deal terms saying senior management of (the) company needs money for backdoor access.”
According to screenshots shared by Krishnan of Xenzen’s correspondence with the company, on July 7, CISO Amarjeet Khanuja, going by the pseudonym mc6, offered to sell the database for USD 35,000. However, the threat actor made a final offering of $28,000, which the CISO apparently agreed to.
Khanuja apparently claimed he wasn’t aware of escrow services – a common way to carry out business in ransomware payments in which a third party (usually a trusted user on database marketplaces who holds on to the funds till the seller and buyer fulfill contractual obligations).
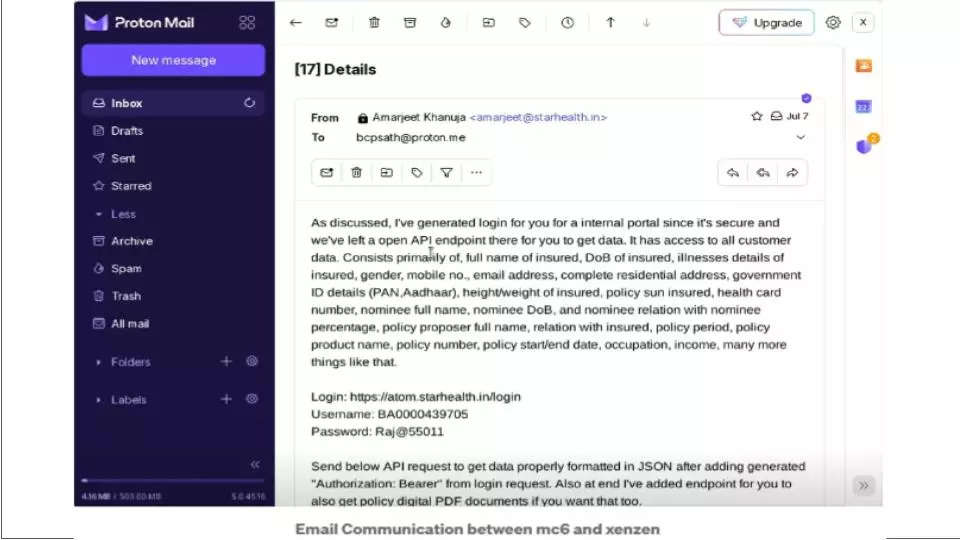
Another screenshot claims that a login for the threat actor was generated for an internal portal and that an API endpoint was left open to exfiltrate the data. A login, username and password was also shared on this mail.
The following day, the supposed insider, mc6, provided his XMR Address to the threat actor.
On July 20, Xenzen additionally requested data about health checkups, which are linked directly to the patient via government ID or photographs. To this, mc6 apparently offered to sell a second database which included insurance claims and rejected applicants’ data. On July 22, the threat actor paid $15,000 and secured access to the second database as well.
The threat actor then claims that he had a fallout with the CISO (mc6) after the latter demanded $150,000 to continue the API access as a portion of this amount would have to be paid to the senior management as well.
Holes in the Story and a CISO Caught in the Crossfire
While the media had a field day throwing CISO Amarjeet Khanuja under the bus based on screenshots shared by the threat actor, Xenzen, cybersecurity researchers point to key pieces of evidence that show that the adversary’s claims are false.
- Clear evidence of an impersonation attack:
Researcher Rakesh Krishnan points out that the entire narrative and media’s subsequent reports tying the CISO to the leak is based on the fact that Khanuja’s official email ID was used to communicate with the threat actor. “This could be an impersonation attack as the insider, likely from the company’s IT team, used the credentials of the CISO.”Anyone from the company’s IT department who has access to database APIs and email ID creation could have easily mimicked CISO, Krishnan adds.
He goes on to explain that this is a tactical approach adopted by insider traders who take a double cover — that of a hacker and an impersonated account to mask his/her identity.
- Actions taken by the CISO look highly improbable:
No CISO would ever risk communicating directly with a threat actor using his/her official email ID. Citing from experience, Krishnan says that CISOs of large organizations seldom know about or control specific database APIs in the company’s IT stack. It’s mostly an IT person with admin access.The cybersecurity chief of a large retail chain adds that CISOs are well aware of the reputational impact a data breach of this scale could have on an organization and that itself is a deterrent.
- Username, password came from a previous credential leak:
Rahul Sasi, co-founder and CEO of cybersecurity firm CloudSEK, in his LinkedIn blog says: “The reality is that the threat actor had faked the email screenshot. The email’s contents were valid, but the username and password allegedly shared by the CISO were actually part of a credential leak from a public darkweb incident.”Beenu Arora, CEO of cybersecurity firm Cyble, also attests that their preliminary analysis traced the compromise of the specified credentials back to an infostealer malware attack on August 4, 2022.
- Threat actor appears to have used an IDOR:
Sasi explains that the threat actor then discovered an Insecure Direct Object Reference (IDOR) in the API after authentication, accessed the data, and then fabricated the story to frame the CISO and the team to defame them. - Threat actor’s prior history targeting India Inc.:
Sasi, in his post, says that the threat actor has shown “vindictive behavior towards Indian citizens in the past and has a history of similar actions.”The statement is in reference to the July 2024 Airtel data breach incident and the alleged leak of the Ministry of External Affairs’ database.
What CISOs can learn from the Star Health Data Breach
A point of concern since the news first broke is how could 7.24 TB of data be exfiltrated without sounding off alarms and what measures CISOs can adopt to be prepared for incidents such as these.
Abhijit Chakravarty, Executive Vice President – Networks & Cyber Security at Kotak Mahindra Bank tells ETCISO that the data leak surely wouldn’t have happened in a single day. “The huge volume of data that was exfiltrated points to lapses in defense and detect capabilities of the organization,” he says.
In his observation, there are many angles of cyber defense that could have helped detect, report and contain. He lists seven key measures CISOs must take to be able to prevent such incidents:
●Stronger access control: privileged access and what is being done with those credentials
●Data leakage/loss prevention strategies: what was deployed and why couldn’t it detect.
●Vulnerability and risk assessments of the IT infra
●User behavior and actions – anomaly detection
●Monitoring and reporting high volume of transactions along with identification of type of data. This being PII data, Chakravarty explains, the controls around it should have been much more stringent
●Real time monitoring, reconciliation & reporting
●Review and governance – lapses around GRC especially of PII data
In addition to this, the CISO of the retail chain advises:
●A log retention policy in which sys logs would have to be retained and maintained for a specific amount of time, which is also a CERT-In requirement at present.
●A job rotation policy that accounts for proper segregation of duties (and)
●Improved attack surface management measures
What Star Health Insurance has to say
Star Health confirmed that it was a victim of a targeted malicious cyberattack, which led to unauthorized access to certain data. The company added that the CISO is cooperating with the investigation and that there has been no finding of wrongdoing against him.
The insurance major faced a fair share of flak when it attempted to sue Telegram and Cloudflare in the wake of the data breach – both of which have thus far been refuted and turned down.
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India













