Top Managed Security Service Providers (MSSP) Top Best Managed Security Service Providers (MSSPs) In 2021 Anyone who is using the internet is exposed to attack. The attack can be of any type, maybe a malware or a type of hacking, spam emails or DDoS attack, etc. When these types of attacks happen to your website, it will have a great ...
Read More »Cyber Security
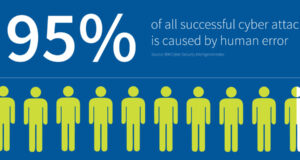
Why Human Error is #1 Cyber Security Threat to Businesses in 2023
Why Human Error is #1 Cyber Security Threat to Businesses in 2023 Phishing and Malware Among the major cyber threats, the malware remains a significant danger. The 2017 WannaCry outbreak that cost businesses worldwide up to $4 billion is still in recent memory, and other new strains of malware are discovered on a daily basis. Phishing has also seen a ...
Read More »Business Email Compromise Groups Springing up in New Locations
Business Email Compromise Groups Springing up in New Locations The Business Email Compromise (BEC) attacks are one the rise globally as new fraud gangs are emerging to trick firms into handing over money. Recently, a security company Agari has detected and analyzed new waves of BEC activities across the globe. What was discovered? As corporate phishing scams have become more ...
Read More »A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems
A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems German authorities last week disclosed that a ransomware attack on the University Hospital of Düsseldorf (UKD) caused a failure of IT systems, resulting in the death of a woman who had to be sent to another hospital that was 20 miles away. The incident marks the first recorded casualty as a ...
Read More »10 Cybersecurity best practices that every employee should know
TOP 10 Cybersecurity best practices that every employee should know If you’re an employee, you are on the front lines of information security. Your company may have comprehensive cybersecurity policies for you and coworkers to follow. But even with these protections, it’s important to stay on guard to help assure your company’s data and network are safe and secure. Does ...
Read More »Cyber Security Best Practices for Business
Cyber Security Best Practices for Business Cyber Security Best Practices for Business, It’s easy to think that because you have a small business, cyber criminals will pass over attacking your company. The “not much to steal” mindset is common with small business owners in regards to cyber security, but it is also completely incorrect and out of sync with today’s ...
Read More »Majority of businesses lack cyber security expertise
Majority of businesses lack cyber security expertise The majority of businesses do not possess adequate cyber security expertise to prevent attacks and protect their customers, a report has found. Specialist insurer His-cox surveyed 4,000 firms in the UK, US, Germany, Spain and the Netherlands, and found 73 per cent were severely lacking in digital security. Around half (45 per cent) ...
Read More »22 TOP Cybersecurity Checklists
22 TOP Cybersecurity Checklists A cybersecurity checklist is important since cybersecurity investments can be a complicated process. An organization must first identify vulnerable assets, determine how vulnerable they are, and allocate sufficient budgets needed to enhance their security. In any cybersecurity program, companies should, at the very least, include the following: Procedures for identifying and assessing cybersecurity threats and risks ...
Read More »Maze Ransomware – What You Need to Know
Maze Ransomware What You Need to Know What’s this Maze thing we keep hearing about? Maze is a particularly sophisticated strain of Windows ransomware that has hit companies and organizations around the world and demanded that a cryptocurrency payment be made in exchange for the safe recovery of encrypted data. There’s been plenty of ransomware before. What makes Maze so ...
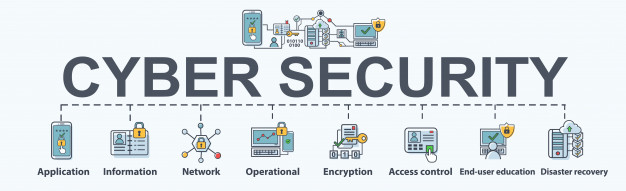
Read More »CYBER SECURITY
CYBER SECURITY – Protect and Secure Your Data Protect and Secure Your Data Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It’s also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided ...
Read More » Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India