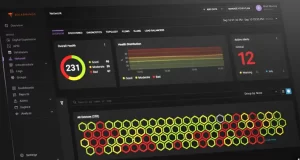
Cybersecurity a strategic imperative for power sector: UP additional Chief Secy Bhooshan https://etimg.etb2bimg.com/thumb/msid-124060571,imgsize-58022,width-1200,height=627,overlay-etciso,resizemode-75/corporate/cybersecurity-a-strategic-imperative-for-power-sector-up-additional-chief-secy-bhooshan.jpg In a strong push to fortify India’s critical infrastructure, Uttar Pradesh’s Additional Chief Secretary for Energy, Narendra Bhooshan, underscored the urgent need for cyber resilience in the power sector during the Conference on Cybersecurity Awareness recently held in Lucknow. “Cybersecurity is no longer just a technical requirement ...
Read More »Cyber Security News
The Future of AI Governance and Critical Infrastructure Security, ETCISO
The Future of AI Governance and Critical Infrastructure Security, ETCISO At the ETCISO Annual Conclave 2025, India’s CISOs explored the growing complexities of digital trust, AI governance, and operational technology security, demonstrating how their roles are evolving far beyond traditional IT defense. In an age where artificial intelligence can empower—or exploit—enterprises, CISOs are increasingly tasked with balancing technological innovation with ...
Read More »Beware of apk files of traffic challans: Cops
Beware of apk files of traffic challans: Cops https://etimg.etb2bimg.com/thumb/msid-123899848,imgsize-16894,width-1200,height=627,overlay-etciso,resizemode-75/data-breaches/beware-of-apk-files-of-traffic-challans-cops.jpg Madurai: Madurai rural district cyber crime police have asked the public to be vigilant against scammers sending apk files for traffic challans and banking KYC updates, or even updates for govt schemes and EB bill payment. Police said that recently, there have been cases of people losing money afters scammers hacked ...
Read More »U.S. Secret Service Seizes 300 SIM Servers, 100K Cards Threatening U.S. Officials Near UN
U.S. Secret Service Seizes 300 SIM Servers, 100K Cards Threatening U.S. Officials Near UN https://firewall.firm.in/wp-content/uploads/2025/09/sim.jpg Sep 23, 2025Ravie LakshmananNational Security / Threat Intelligence The U.S. Secret Service on Tuesday said it took down a network of electronic devices located across the New York tri-state area that were used to threaten U.S. government officials and posed an imminent threat to national ...
Read More »Data from 20 private equity funds leaked in hacking attack in S. Korea
Data from 20 private equity funds leaked in hacking attack in S. Korea https://etimg.etb2bimg.com/thumb/msid-124060596,imgsize-24508,width-1200,height=627,overlay-etciso,resizemode-75/data-breaches/data-from-20-private-equity-funds-leaked-in-hacking-attack-in-s-korea.jpg Seoul, Data from around 20 asset management firms in South Korea were breached in a hacking incident earlier this month, industry sources said on Monday. A cloud server maintained by an IT subcontractor and used mostly by local small and medium-sized private equity funds was hacked ...
Read More »Kaspersky and GRAMAX Collaborate to Empower Women in Cybersecurity, ETCISO
Kaspersky and GRAMAX Collaborate to Empower Women in Cybersecurity, ETCISO The event, titled Resilience in Action: The Women Beyond The Firewalls, focused on the current landscape for women in technology, underscoring both the progress made and the roadblocks that remain. According to Kaspersky’s previous Women in Tech report, 56% of women in tech observe a positive shift in gender equality ...
Read More »South Korea: Presidential office to unveil cybersecurity measures following hacking incidents
South Korea: Presidential office to unveil cybersecurity measures following hacking incidents https://etimg.etb2bimg.com/thumb/msid-124060607,imgsize-12854,width-1200,height=627,overlay-etciso,resizemode-75/data-breaches/south-koreas-presidential-office-unveils-comprehensive-cybersecurity-measures-to-combat-hacking.jpg Seoul, The presidential Office of National Security said Monday it will come up with “comprehensive” measures to prevent further hacking incidents following a series of security breaches at mobile carriers and a credit card issuer. The presidential office said it has been in consultations with relevant ministry officials ...
Read More »SolarWinds Releases Hotfix for Critical CVE-2025-26399 Remote Code Execution Flaw
SolarWinds Releases Hotfix for Critical CVE-2025-26399 Remote Code Execution Flaw https://firewall.firm.in/wp-content/uploads/2025/09/solar.jpg Sep 23, 2025Ravie LakshmananVulnerability / Data Security SolarWinds has released hot fixes to address a critical security flaw impacting its Web Help Desk software that, if successfully exploited, could allow attackers to execute arbitrary commands on susceptible systems. The vulnerability, tracked as CVE-2025-26399 (CVSS score: 9.8), has been described ...
Read More »NPCI’s RASP Mandate: Why Mobile App Security Is No Longer Optional — and How DoveRunner Leads the Way
NPCI’s RASP Mandate: Why Mobile App Security Is No Longer Optional — and How DoveRunner Leads the Way https://etimg.etb2bimg.com/thumb/msid-124065666,imgsize-6388,width-1200,height=627,overlay-etciso,resizemode-75/brand-solution/npcis-rasp-mandate-why-mobile-app-security-is-no-longer-optional-and-how-doverunner-leads-the-way.jpg India’s payments ecosystem, powered by UPI, has transformed everyday transactions into a seamless experience. But as billions of payments move through mobile apps each day, attackers are exploiting weak points in these very apps to commit fraud, steal data, and undermine ...
Read More »Key highlights from ETCISO Annual Conclave 2025, ETCISO
Key highlights from ETCISO Annual Conclave 2025, ETCISO The conclave opened with the launch of the Cybersecurity Leadership Report 2025, presented by Shantheri Mallaya, Editor, ETCISO, and Krishna Mukherjee, Senior Lead, Editorial & Community, ETCIO. Key findings showed India’s security investments shifting from capex-heavy defenses to agile, cloud-first resilience models. Budgets are moving toward opex with SaaS, XDR, and MDR ...
Read More » Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India