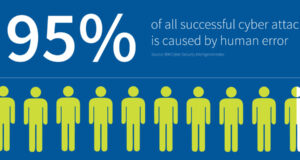
Why Human Error is #1 Cyber Security Threat to Businesses in 2023 Phishing and Malware Among the major cyber threats, the malware remains a significant danger. The 2017 WannaCry outbreak that cost businesses worldwide up to $4 billion is still in recent memory, and other new strains of malware are discovered on a daily basis. Phishing has also seen a ...
Read More »Endpoint security
Business Email Compromise Groups Springing up in New Locations
Business Email Compromise Groups Springing up in New Locations The Business Email Compromise (BEC) attacks are one the rise globally as new fraud gangs are emerging to trick firms into handing over money. Recently, a security company Agari has detected and analyzed new waves of BEC activities across the globe. What was discovered? As corporate phishing scams have become more ...
Read More »A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems
A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems German authorities last week disclosed that a ransomware attack on the University Hospital of Düsseldorf (UKD) caused a failure of IT systems, resulting in the death of a woman who had to be sent to another hospital that was 20 miles away. The incident marks the first recorded casualty as a ...
Read More »Sophos Antivirus End Points
Sophos Antivirus End Point Protection Sophos End Points June 2017 Sophos Authorized Partner July 2020 Sophos Silver Partner Sophos Antivirus End Point Protection For Client Central End Point Protection Anti Virus For 1 Year Rs. 1150 + 18% GST Central End Point Protection Anti Virus For 3 Year Rs. 2,300 + 18% GST Central End Point Intercept X Ransomware ...
Read More »End User End Points Protection
End User End Point Protection JUNIPER ANTIVIRUS END POINTS Enforce Policies and Configure Endpoint Security with Junos OS Enforcer In a Unified Access Control (UAC) environment, after an SRX Series device becomes Junos OS Enforcer, the SRX Series device allows or denies traffic based on Junos OS security policy. Infranet agent runs on the endpoints to secure traffic by checking ...
Read More »How to Protect firewalls from hacking ?
Can Firewalls be Hack ? The short answer is: “YES.” How to Protect firewalls from hacking ? Firewall security measures are one of the most basic cyber protection tools that organizations of all sizes use to prevent data breaches and hacking. Network security firewalls filter out incoming traffic to prevent malicious files from being downloaded and block attackers from accessing ...
Read More »Network Operations Center – NOC Services in India
Network Operations Center – NOC Services in India A network operations center! NETWORK OPERATIONS CENTER SERVICES In India A network operations center or NOC Services in India is a single location where a firm and its employees can provide oversight 24 hours a day, seven days a week to help oversee and manage services, databases, external services, firewalls, and the ...
Read More »NETWORK OPERATIONS CENTER SERVICES In India
Network Operations Center NOC Services in India A network operations center! NETWORK OPERATIONS CENTER SERVICES In India A network operations center or NOC Services in India is a single location where a firm and its employees can provide oversight 24 hours a day, seven days a week to help oversee and manage services, databases, external services, firewalls, and the company’s ...
Read More » Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India