Fake Reliance Jio Tower malicious app capable of stealing financial data, PII

Researchers at cybersecurity firm Technisanct have discovered a banking Trojan named JioTower.apk that is capable of stealing financial and personal data from infected devices.
The fake app is doing the rounds via a phishing website: https://rewardapps[.]xyz. The website masquerades as a reward app. After a user clicks on the URL, they are directed to download a Reliance Jio Tower mobile application. The app is essentially a banking malware that uses Jio Tower branding to appear legitimate.
Malware capabilities
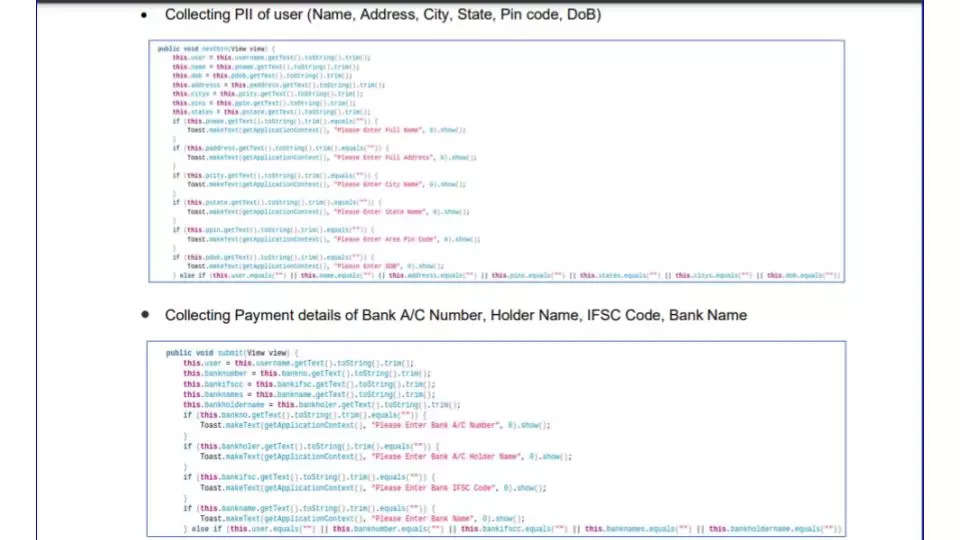
The malware, Technisanct researchers tell ETCISO, is equipped to steal all SMS messages on the user’s device, their personally identifiable information or PII, Aadhaar & PAN card numbers, bank card details, and OTPs sent to the device.
“The malware seeks 10 permissions from the user and abuses four of these,” they say.
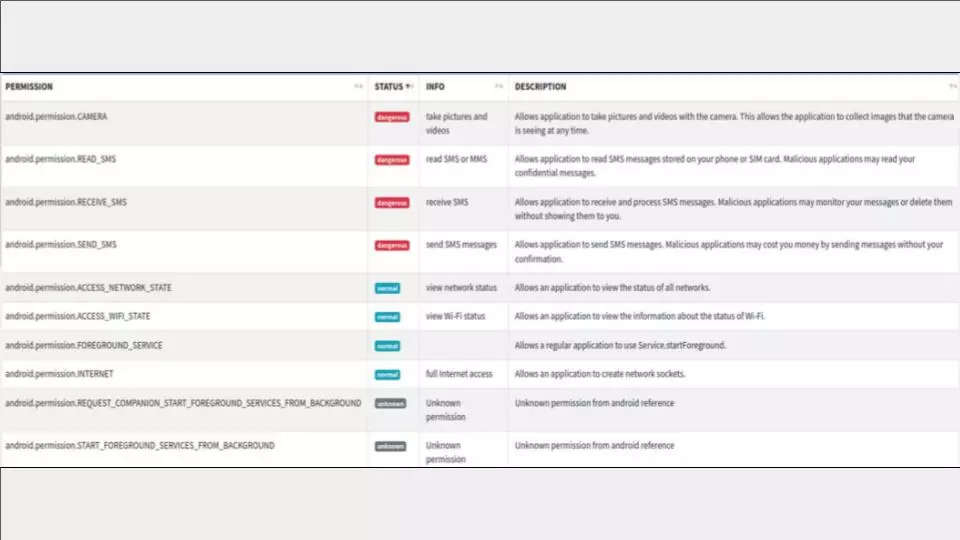
The permissions that are particularly risky are: camera access and the permissions to read, receive and send SMSs.
In addition to SMS access, the malware grants permissions to contacts, call logs and device location. “Based on instructions received from the malware writers’ command & control server, the infection not only records calls and audio but also deletes files, places calls, and takes photographs with the camera,” researchers say.
Code analysis reveals that the malware is collecting hardcoded sensitive information, such as usernames, passwords, and keys. Its capabilities extend to collecting banking information – bank account number, account holder’s name, IFSC Code, and credit/debit card details as well.
To keep targeted users from being notified about suspicious activities or transactions, the malware puts all notifications to silent mode.
For lateral movement, the malware exploits remote desktop protocol – RDP (MITRE ATT&CK technique: T1021.001).
With the help of RDP, threat actors use valid accounts to log into a computer, following which they execute actions as a legitimate logged-on user. A common technique to maintain persistence is by using the RDP with ‘Accessibility Features’ or ‘Terminal Services DLL’.
For some time now, RDP has been a ‘weapon of choice’ for many prolific threat groups such as Cobalt Strike, jRAT, Lazarus Group, and Pysa, to name a few.
Impact
Technisanct researchers tell us that owing to its extensive SMS theft capabilities, hackers can utilise the compromised data to steal from other banking apps on the user’s device.
“The protections offered by banks’ two-factor authentication procedures, which customers and institutions rely on to keep their transactions secure, are thwarted by its capacity to intercept one-time passwords (OTPs) supplied over SMS,” they explain.
Banking Trojans are quite the favorite on dark web forums. Researchers warn that threat actors market these Trojans and propagate them through numerous websites and third-party retailers.
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India











