Malicious Ads on Google Target Chinese Users with Fake Messaging Apps

Chinese-speaking users have been targeted by malicious Google ads for restricted messaging apps like Telegram as part of an ongoing malvertising campaign.
“The threat actor is abusing Google advertiser accounts to create malicious ads and pointing them to pages where unsuspecting users will download Remote Administration Trojan (RATs) instead,” Malwarebytes’ Jérôme Segura said in a Thursday report. “Such programs give an attacker full control of a victim’s machine and the ability to drop additional malware.”
It’s worth noting that the activity, codenamed FakeAPP, is a continuation of a prior attack wave that targeted Hong Kong users searching for messaging apps like WhatsApp and Telegram on search engines in late October 2023.
The latest iteration of the campaign also adds messaging app LINE to the list of messaging apps, redirecting users to bogus websites hosted on Google Docs or Google Sites.
The Google infrastructure is used to embed links to other sites under the threat actor’s control in order to deliver the malicious installer files that ultimately deploy trojans such as PlugX and Gh0st RAT.
Malwarebytes said it traced the fraudulent ads to two advertiser accounts named Interactive Communication Team Limited and Ringier Media Nigeria Limited that are based in Nigeria.
“It also appears that the threat actor privileges quantity over quality by constantly pushing new payloads and infrastructure as command-and-control,” Segura said.
The development comes as Trustwave SpiderLabs disclosed a spike in the use of a phishing-as-a-service (PhaaS) platform called Greatness to create legitimate-looking credential harvesting pages targeting Microsoft 365 users.
“The kit allows for personalizing sender names, email addresses, subjects, messages, attachments, and QR codes, enhancing relevance and engagement,” the company said, adding it comes with anti-detection measures like randomizing headers, encoding, and obfuscation aim to bypass spam filters and security systems.
Greatness is offered for sale to other criminal actors for $120 per month, effectively lowering the barrier to entry and helping them conduct attacks at scale.
Attack chains entail sending phishing emails bearing malicious HTML attachments that, when opened by the recipients, direct them to a fake login page that captures the login credentials entered and exfiltrates the details to the threat actor via Telegram.
Other infection sequences have leveraged the attachments to drop malware on the victim’s machine to facilitate information theft.
To increase the likelihood of success of the attack, the email messages spoof trusted sources like banks and employers and induce a false sense of urgency using subjects like “urgent invoice payments” or “urgent account verification required.”
“The number of victims is unknown at this time, but Greatness is widely used and well-supported, with its own Telegram community providing information on how to operate the kit, along with additional tips and tricks,” Trustwave said.
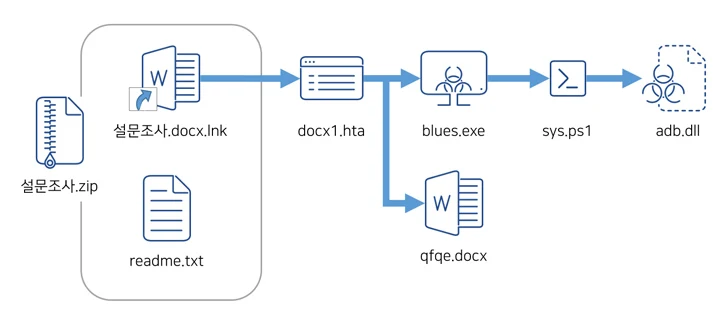
Phishing attacks have also been observed striking South Korean companies using lures that impersonate tech companies like Kakao to distribute AsyncRAT via malicious Windows shortcut (LNK) files.
“Malicious shortcut files disguised as legitimate documents are continuously being distributed,” the AhnLab Security Intelligence Center (ASEC) said. “Users can mistake the shortcut file for a normal document, as the ‘.LNK’ extension is not visible on the names of the files.”
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India











