Security researchers have discovered a new class of security vulnerabilities that impacts all major operating systems, including Microsoft Windows, Apple macOS, Linux, and FreeBSD, allowing attackers to bypass protection mechanisms introduced to defend against DMA attacks.
Known for years, Direct memory access (DMA)-based attacks let an attacker compromise a targeted computer in a matter of seconds by plugging-in a malicious hot plug device—such as an external network card, mouse, keyboard, printer, storage, and graphics card—into Thunderbolt 3 port or the latest USB-C port.
The DMA-based attacks are possible because Thunderbolt port allows connected peripherals to bypass operating system security policies and directly read/write system memory that contains sensitive information including your passwords, banking logins, private files, and browser activity.
That means, simply plugging in an infected device, created using tools like Interception, can manipulate the contents of the memory and execute arbitrary code with much higher privileges than regular universal serial bus peripherals, allowing attackers to bypass the lock screen or control PCs remotely.
To block DMA-based attacks, most operating systems and devices leverage Input/Output Memory Management Unit (IOMMU) protection technique to control which peripheral device (usually legitimate) can access memory and which region of the memory.
ThunderClap Flaws Bypass IOMMU to Re-Enable DMA Attacks
Now, a team of cybersecurity researchers from the University of Cambridge, Rice University, and SRI International has unveiled a set of new vulnerabilities in various major operating systems that could allow attackers to bypass IOMMU protection.
By mimicking the functionality of a legitimate peripheral device, an attacker can trick targeted operating systems into granting it access to sensitive regions of memory.
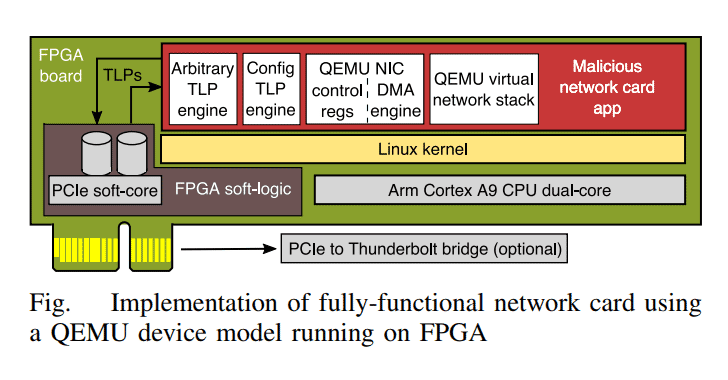
In a paper [PDF] published earlier this week, researchers detailed technical information of all new vulnerabilities that they claimed to have discovered using a hardware/software stack, called Thunderclap, which they build and also released in the open-source.
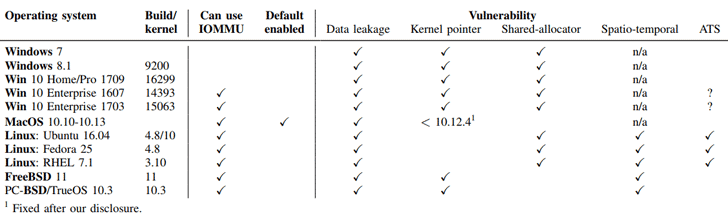
Besides this, the researchers also stressed that since IOMMU does not come enabled by default on most operating systems and since modern devices have USB-C, the attack surface of DMA attack has significantly increased which was earlier primarily limited to Apple devices with Thunderbolt 3 ports.
“The rise of hardware interconnects like Thunderbolt 3 over USB-C that combine power input, video output, and peripheral device DMA over the same port greatly increases the real-world applicability of Thunderclap vulnerabilities.”
“In particular, all Apple laptops and desktops produced since 2011 are vulnerable, with the exception of the 12-inch MacBook. Many laptops, and some desktops, designed to run Windows or Linux produced since 2016 are also affected – check whether your laptop supports Thunderbolt.”
How to Protect Against Thunderclap Vulnerabilities
Researchers have reported their findings to all major hardware and operating system vendors, and most of them have already shipped substantial mitigation to address the Thunderclap vulnerabilities.
“In macOS 10.12.4 and later, Apple addressed the specific network card vulnerability we used to achieve a root shell,” researchers said. “Recently, Intel has contributed patches to version 5.0 of the Linux kernel.”
“The FreeBSD Project indicated that malicious peripheral devices are not currently within their threat model for security response.”
Though not all software patches can entirely block DMA attacks, users are still advised to install available security updates to reduce the attack surface. According to the researchers, the best way to fully protect yourself is to disable the Thunderbolt ports on your machine, if applicable.
Additionally, researchers also developed a proof-of-concept attacking hardware that can execute the ThunderClap vulnerabilities on targeted systems, but they chose not to release it in public at this time.
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India