What is Nudge Security and How Does it Work?
In today’s highly distributed workplace, every employee has the ability to act as their own CIO, adopting new cloud and SaaS technologies whenever and wherever they need. While this has been a critical boon to productivity and innovation in the digital enterprise, it has upended traditional approaches to IT security and governance.
Nudge Security is the world’s first and only solution to address SaaS security and governance at scale by working with employees—not against them. Unlike legacy solutions that attempt to block employees’ access to unsanctioned SaaS applications, Nudge Security helps IT and security leaders adapt and align to the needs of the business. The platform orchestrates SaaS administration without sacrificing visibility, centralized governance, or control over the organization’s cloud and SaaS security posture.
How Nudge Security works
Nudge Security discovers all SaaS accounts ever created by anyone in your organization within minutes of starting a free trial, and only requires a single point of integration: read-only API access to your Microsoft 365 or Google Workspace email provider. No endpoint agents, network proxies, browser plugins, app integrations, or other complicated deployment steps required.
The patented approach to SaaS discovery takes advantage of a consistent design pattern: every SaaS provider uses email to drive user engagement, making it the perfect event log to capture new account sign-ups and other security-relevant activities. By searching and analyzing machine-generated email messages (e.g., no-reply@box.com), Nudge Security builds and updates your inventory of SaaS accounts, users, and resources, without you ever having to tell it which apps to look for.
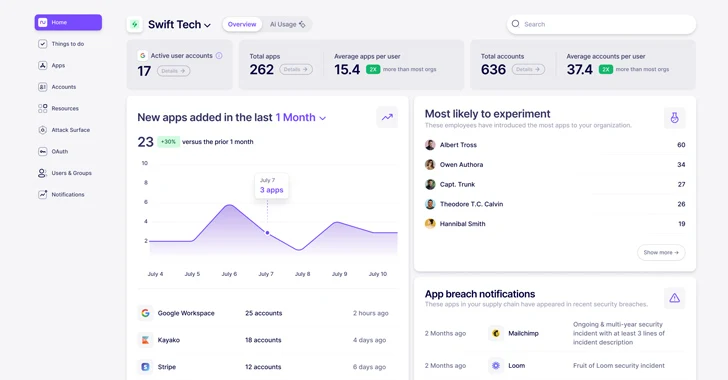
 |
| Inventory of SaaS users and apps |
Implement SaaS security best practices
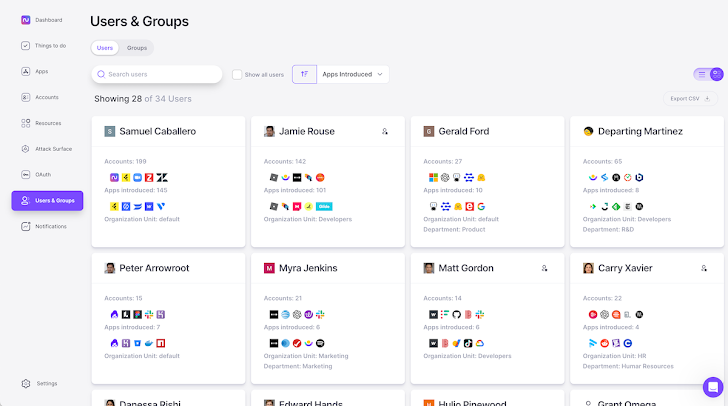
Nudge Security not only shows you who has access to what, but it includes valuable context on how access was granted, whether through SSO, an OAuth grant, or username and password. Nudge Security also shows you which apps and accounts are (and aren’t) enrolled in MFA or SSO so you can easily track progress against your enrollment efforts and kick off automated workflows to help users enable MFA for their accounts and enroll apps in SSO.
Additionally, you’ll see a full inventory of all OAuth grants and scopes to understand where app-to-app integrations could allow data to be shared beyond what is permissible under your data governance policy. OAuth risk scores help you quickly identify overly permissive scopes so you can nudge app users for more context, or revoke the grant with two clicks.
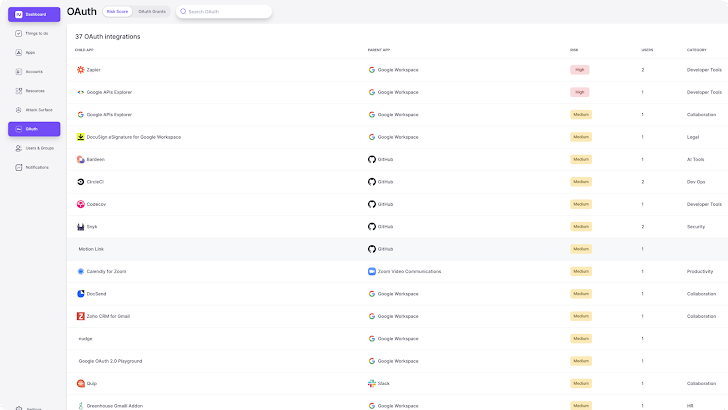 |
| List of OAuth grants and scopes |
Monitor your SaaS attack surface
Your modern attack surface extends to every SaaS app, user identity, and OAuth grant used by your workforce to build your products and run your business. That’s why Nudge Security discovers and monitors your entire SaaS attack surface as it changes, including SaaS apps, cloud infrastructure, developer tools, social media accounts, registered domains and more. With Nudge Security, you can see all externally facing assets an attacker could see so you can take proactive steps to protect and minimize your attack surface.
Nudge Security also provides vendor security profiles for each of your SaaS providers, including breach history, compliance attestations, data locality, and more. With this data, you can conduct SaaS vendor security assessments more quickly and prepare for compliance audits more easily. And, only Nudge Security shows you the SaaS supply chain of your SaaS vendors, so when breaches of high profile apps occur you can quickly determine if you are in the blast radius of a third- or fourth-party supply chain attack. You’ll even be alerted if a SaaS provider you use is breached, or if a SaaS tool used by one of your providers is breached.
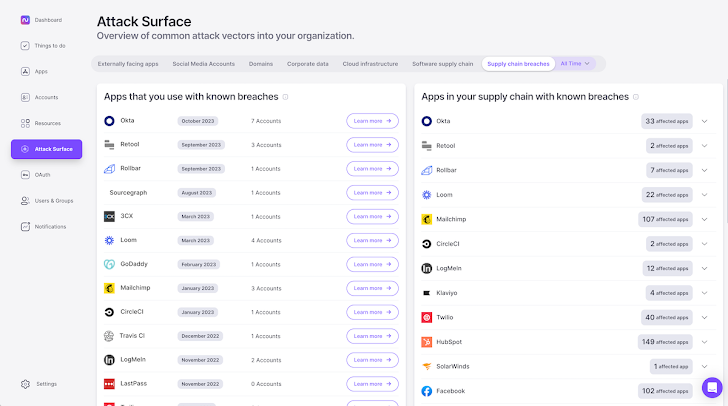 |
| Breach history for your apps and those used by your SaaS providers |
Rein in SaaS sprawl without impeding productivity
Research shows that limiting employees’ access to SaaS applications in an effort to curb SaaS sprawl leads to frustration and shadowy workarounds.
Nudge Security automates employee engagement with timely, helpful nudges that guide users and application owners toward SaaS security best practices. For example, when a new app is discovered, you can ask the user how they will be using it, or nudge them to use an approved alternative. You can also nudge users to ask if they are still using a particular app so you can reclaim unused licenses. These automated touchpoints make it simple to orchestrate SaaS security and governance at scale, driving increased IT efficiency.
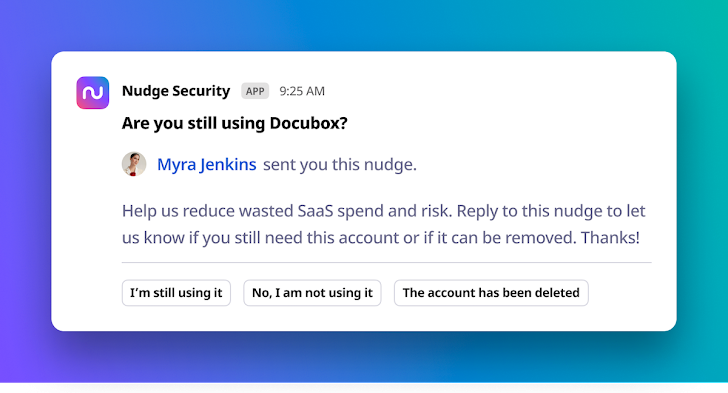 |
| Nudges users to find out what apps they still need |
Automate your SaaS security efforts.
The last thing you need is another security product that creates overhead for your team. Our built-in playbooks automate workflows for common SaaS security tasks, like conducting user access reviews, bringing AWS accounts into central governance organizations, offboarding departing employees, revoking risky OAuth grants, and more so you can minimize time spent on tedious manual tasks.
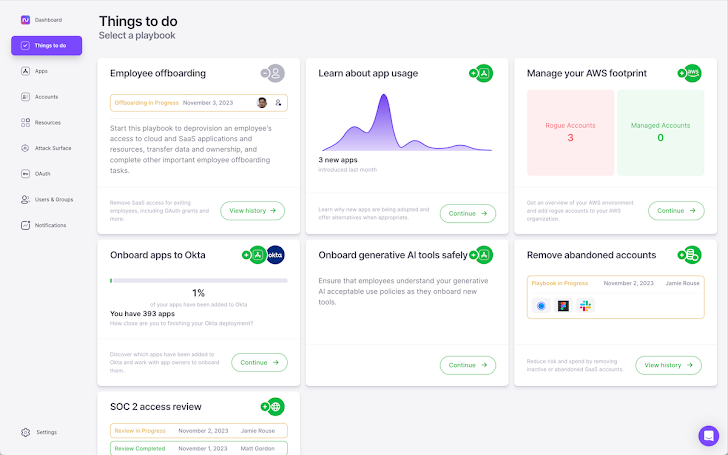 |
| Playbooks automate common SaaS administration tasks |
Get started with Nudge Security.
To discover your organization’s SaaS footprint and modernize your approach to SaaS security and governance, start your 14-day free trial today.
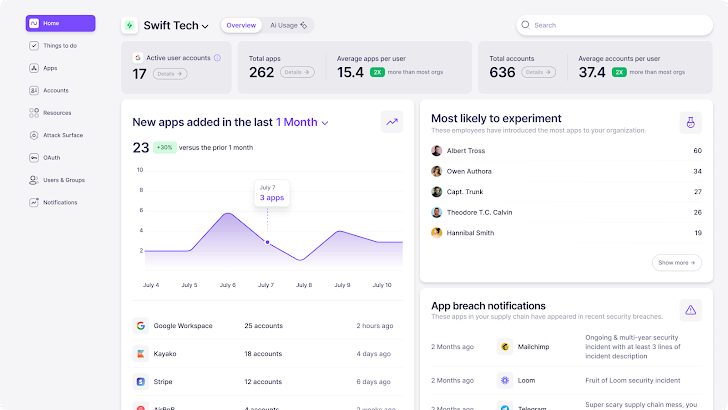 |
| Your SaaS management dashboard in Nudge Security |
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India











