Hardware Firewall Devices
Firewall Devices
Hardware firewalls come in a variety of types. There are commercially available systems that can cost thousands of dollars and are used by network administrators to control any size network. The most commonly available routers for general use are the types that connect to the average Small Office/Home Office (SOHO) network. They are small, easily configurable routers which contain firmware that allow for simple user configuration. They are specifically intended for SOHO use with DSL or cable modem connections. Most have a wireless capability installed as a feature on the router which allows the use of a laptop, or other device, anywhere within the range of the wireless router. Range from which a device can connect through the wireless function depends greatly on the make and model of the firewall. Routers also allow the investigator to distribute their broadband Internet connection between multiple computers. Putting together a SOHO network allows your investigative team to back up computer’s files on networked computers or storage devices in case an infected machine needs to be restored. Additionally, routers often have features that can be of potential use to the online investigator such as logging
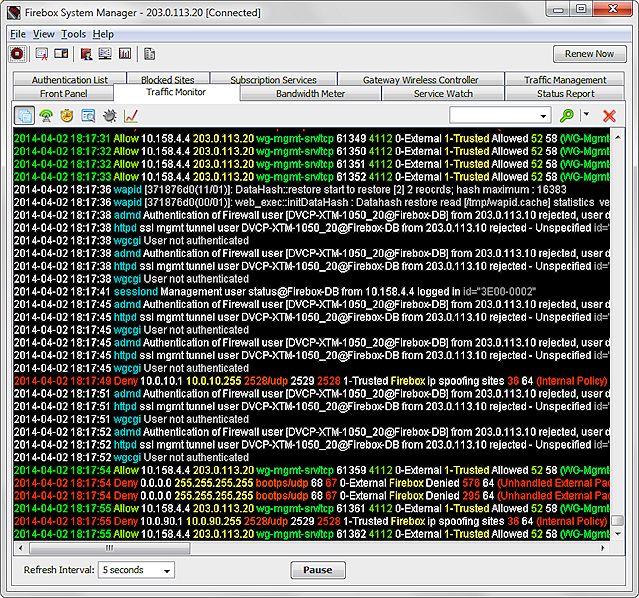
Firewall Device Log Messages (Traffic Monitor)
The logging feature can assist the investigator in the identification of attempted, or successful, intrusions into their investigative system or network. The logs can also identify when investigative systems accessed the Internet and potentially where on the Internet the systems went. Each router and its configuration are different. Be sure to read the manufacturers’ manual to identify individual device features. At a minimum, the following common steps should be considered for router security:
1. Enable encryption: Current SOHO routers generally have Wired Equivelent Privacy (WEP) (an older hackable encryption system), Wi-Fi Protected Access (WPA) preferable, or WPA2 encryption. Ensure you turn on the encryption and use a strong password/passkey; otherwise, anyone with a wireless card could connect to your wireless access. If available, choose WPA-PSK (pre-shared key) and use a strong password/key.
2. Change the service set identifier (SSID)/disable broadcast: If you enable the wireless function, the default SSID (or wireless name for your access point) for your router needs to be changed to something unique to your system and does not identify the organization. The default SSID name makes it easier for hackers to identify and exploit your system. Disable the SSID broadcast so it cannot be seen. This will make your system stealthier and harder to discover. Simply turning off this function can prevent attack issues from the wireless feature.
3. Remote management: Turn off remote management. Sometimes called Wide Area Network (WAN) Management. This feature lets you change the router’s settings from the Internet. It’s an excessive risk and one that does not need to be taken.
4. Change the access password to your router: The default password for your router can probably be found on the Internet. Select a strong password of at least eight characters, using a combination of letters, numbers, and symbols. The password selected should not be a word easily found in the dictionary.
5. Disable Universal Plug and Play on the router.
6. Media Access Control (MAC): A good security option is MAC addressing. This ties hardware device addresses for each computer to a specific network subnet address (as assigned by your router) associated with your machine in order to validate the devices. It prevents unauthorized access to your network by unknown hardware.
7. Ping: Uncheck any options that allow the router to respond to a ping command from the Internet. No need to let anyone know your router is online.
Default Passwords
Most hackers know the default passwords for commonly sold routers and it has become a known exploit. Those that don’t know them can find them on websites, such as Router passwords.com and just look them up. A strong password is at least 8–12 characters, including letters, numbers, and symbols. The longer the password the better! Do not use words found in the dictionary or common names. These can make a brute force attack to crack the password successful. Store the password in a safe place in case changes need to be made to the router.
The inclusion of the software mentioned here is for the reader’s use. The authors have no interest in the software referenced in this chapter. Many software packages of a similar nature exist and new products are deployed regularly. Many of the vendors provide applications that provide blended protection, such as including a firewall, anti-malware, and data backup functions in one package. The reader should use the software mentioned as a starting point and research current versions and other software for potential use on the investigative computer system. Good research sites for reviews on protective tools are CNET (http://www.cnet.com), PC World (http://www.pcworld.com), and SC Magazine (http://www.scmagazine.com). These sites routinely evaluate, compare, and publish the results on protective software and hardware firewall device. Be careful with “free” versions of anything. Most of them come with some adware or tracking software which could expose an investigator.
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India











