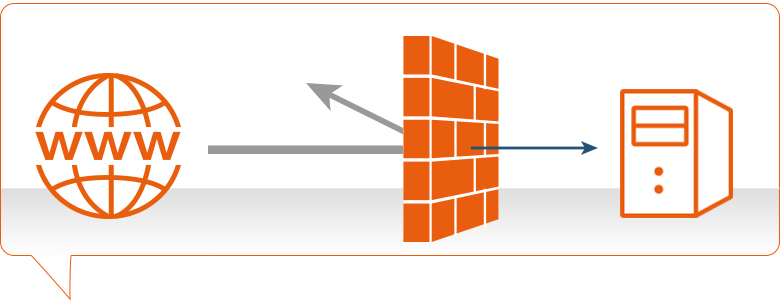
Firewall Training
Best Firewall Training & Workshops for Palo Alto, checkpoint (CCSA | CCSE ), CCNA Course, Cisco, BIG IP/F5, Juniper(JNCIA | JNCIS | JNCIP), Fortinet’s Fortigate Firewalls, Cisco Fire Power Firewalls, Sonicwall Firewalls, Barracuda Firewalls, H3C Firewalls, Check Point Firewalls, Paloalto Firewalls, Cyberoam Shohos Firewalls, Juniper Firewalls, Forcepoint Firewalls, Huawei Firewalls, Watchguard Firewalls, Hilstone Firewalls Firewall Training Institute in Delhi NCR India
Firewall Training – Best Firewall Training & Workshops for Palo Alto, checkpoint (CCSA | CCSE ), CCNA Course, Cisco, BIG IP/F5, Juniper(JNCIA | JNCIS | JNCIP), Fortinet’s Fortigate Firewalls, Cisco Fire Power Firewalls, Sonicwall Firewalls, Barracuda Firewalls, H3C Firewalls, Check Point Firewalls, Paloalto Firewalls, Cyberoam Shohos Firewalls, Juniper Firewalls, Forcepoint Firewalls, Huawei Firewalls, Watchguard Firewalls, Hilstone Firewalls Firewall Training Institute in Delhi NCR India
Fortinet Network Security Expert Program (NSE)
The Fortinet Network Security Expert (NSE) Program
The Fortinet Network Security Expert (NSE) is an eight-level certification program designed for technical professionals interested in independent validation of their network security skills and experience. The program includes a wide range of self-paced and instructor-led courses, as well as practical, experiential exercises that demonstrate mastery of complex network security concepts.
To earn certification at each of the levels, you must pass a series of quizzes or exams. For NSE 1-3, the quizzes are incorporated into the self-paced learning packages hosted in the NSE Institute portal. A third-party vendor, Pearson VUE, proctors the exams for NSE 4-8. You can register for these exams online. To become NSE 8 certified, you must pass the written exam hosted by Pearson VUE, plus a practical exam hosted by Fortinet.
All NSE certification levels are valid for 2 years.
Benefits of Completing the NSE Program
NSE certification will help you to:
- Be recognized in the industry among an elite group of security professionals.
- Validate your network security skills and experience.
- Demonstrate value to current and future employers.
- Leverage Fortinet’s full range of network security products, consolidate solutions, and reduce risks.
- As a partner, accelerate sales and offer new services.
NSE Program Overview
Successful completion of the NSE Program involves meeting the following objectives for each level. Click on a level course name to get more information about how to certify at that level or the course description.
| Level |
Objective
|
Certification
|
Courses
|
|---|---|---|---|
|
Develop a foundational understanding of the Threat Landscape and perspectives from key executive roles. Also learn how individuals can be safer on the Internet with Personal Security Awareness.
|
Complete the NSE 1 course.
|
The Threat Landscape
|
|
|
Discover the types of security products that have been developed to address the threat landscape discussed in NSE 1.
|
Complete the NSE 2 course.
|
The Evolution of Cybersecurity
|
|
|
Develop the skills to describe how the features of key Fortinet products solve customer problems.
|
Complete any four NSE 3 courses.
|
Fortinet Core Products*
|
|
|
Develop the knowledge to manage the day-to-day configuration, monitoring, and operation of FortiGate devices to support corporate network security policies.
|
Passing the NSE 4 exam at a PearsonVUE testing center.
|
FortiGate Security
FortiGate Infrastructure
|
|
|
Develop a detailed understanding of how to implement network security management and analytics.
|
Passing any two NSE 5 exams at a PearsonVUE testing center.
|
FortiAnalyzer
FortiManager
FortiSIEM
FortiInsight (formerly Zonefox)
FortiClient EMS
|
|
|
Develop an understanding of the fabric products that augment FortiGate to provide deeper and more comprehensive network security.
|
Passing any four NSE 6 exams at a PearsonVUE testing center.
|
FortiADC FortiAuthenticator
FortiDDoS FortiMail
FortiNAC FortiWiFi
FortiWeb FortiWLC
|
|
|
Develop the knowledge to integrate Fortinet products to deploy and administrate network security solutions.
|
Passing any NSE 7 exam at a PearsonVUE testing center.
|
Advanced Threat Protection
Enterprise Firewall
Secure Access
Public Cloud Security
|
|
|
Demonstrate the ability to design, configure, install, and troubleshoot a comprehensive network security solution in a live environment.
|
Passing both, the NSE 8 written exam at a PearsonVUE testing center and then, the NSE 8 practical exam at Fortinet.
|
No preparation course
|
Sophos Firewall Training for IT Admins
For IT Admin who are using Sophos Firewall, want to make sure you get the best from your investment. Our Sophos Administrator courses are designed to do just that. We are a Sophos Partner and we can help you to buy a course and you’ll be on the way to sharpening your product know-how while simplifying your job as an administrator. On completion, you’ll understand key product capabilities and how they protect your organization. Available courses include Endpoint, UTM Training, XG Firewall, and SafeGuard and cover how to:
- Manage security events
- Backup and restore the system
- Complete common day-to-day tasks
- View, manage, and interpret logs and reports
- Perform basic troubleshooting
Check out our resources:
CCNSP is the certification for security professionals from Cyberoam firewall. The only Identity-based security certification available globally the course prepares individuals to recognize insider threats and user-targeted external threats while giving them expertise in networking and security fundamentals in addition to the deployment and configuration of Cyberoam identity-based UTM. The course is comprehensive, yet easy to follow, with real world scenarios, delivering practical value to aspiring security professionals.
Prerequisites:
While the course does not have any pre-requisites, security professionals interested in enrolling need to be familiar with networking concepts, including network topologies, networking infrastructure and application protocols:
Operational OS knowledge
Basics of Networking
Knowledge of Protocols
HTTP, HTTPS, IMAP, POP3, SMTP
TCP/IP Protocol Suite
Network Security Fundamentals
Operational Familiarity with Featured Modules
Firewall, VPN, IPS, Anti-virus, Anti-spam, Content Filtering, Bandwidth Management, Multiple Link Management, Reporting
Who Should Attend:
CCNSP has been designed for technical professionals providing support or performing deployment and administration of Cyberoam solutions, including System, Network, and Security Administrators.
CCNSP training is divided into the following modules –
• Labs
• Labs to provide hands on to deal with maintenance
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India