Microsoft Warns of Widening APT29 Espionage Attacks Targeting Global Orgs Jan 26, 2024NewsroomThreat Intelligence / Cyber Attack Microsoft on Thursday said the Russian state-sponsored threat actors responsible for a cyber attack on its systems in late November 2023 have been targeting other organizations and that it’s currently beginning to notify them. The development comes a day after Hewlett Packard Enterprise ...
Read More »Blog
Malicious Ads on Google Target Chinese Users with Fake Messaging Apps
Malicious Ads on Google Target Chinese Users with Fake Messaging Apps Jan 26, 2024NewsroomMalvertising / Phishing-as-a-service Chinese-speaking users have been targeted by malicious Google ads for restricted messaging apps like Telegram as part of an ongoing malvertising campaign. “The threat actor is abusing Google advertiser accounts to create malicious ads and pointing them to pages where unsuspecting users will download ...
Read More »Perfecting the Defense-in-Depth Strategy with Automation
Perfecting the Defense-in-Depth Strategy with Automation Medieval castles stood as impregnable fortresses for centuries, thanks to their meticulous design. Fast forward to the digital age, and this medieval wisdom still echoes in cybersecurity. Like castles with strategic layouts to withstand attacks, the Defense-in-Depth strategy is the modern counterpart — a multi-layered approach with strategic redundancy and a blend of passive ...
Read More »AllaKore RAT Malware Targeting Mexican Firms with Financial Fraud Tricks
AllaKore RAT Malware Targeting Mexican Firms with Financial Fraud Tricks Jan 27, 2024NewsroomMalware / Software Update Mexican financial institutions are under the radar of a new spear-phishing campaign that delivers a modified version of an open-source remote access trojan called AllaKore RAT. The BlackBerry Research and Intelligence Team attributed the activity to an unknown Latin American-based financially motivated threat actor. ...
Read More »Sophos XGS Firewall
Sophos XGS Firewall Buy Sophos XGS Firewall online from Firewall Firm’s IT Monteur Store Sophos Firewall Sophos XGS Firewall (Small Office) Sophos XGS 87 / 87w Firewall Users: 10 Firewall: 3.6 GBPS NGFW: 700 MBPS IPSEC VPN: 2800 MBPS IPS: 1015 MBPS Sophos XGS 107 / 107w Firewall Users: 25 Firewall: 6.8 GBPS NGFW: 1050 MBPS IPSEC VPN: 4000 MBPS ...
Read More »Kasseika Ransomware Using BYOVD Trick to Disarms Security Pre-Encryption
Kasseika Ransomware Using BYOVD Trick to Disarms Security Pre-Encryption The ransomware group known as Kasseika has become the latest to leverage the Bring Your Own Vulnerable Driver (BYOVD) attack to disarm security-related processes on compromised Windows hosts, joining the likes of other groups like Akira, AvosLocker, BlackByte, and RobbinHood. The tactic allows “threat actors to terminate antivirus processes and services ...
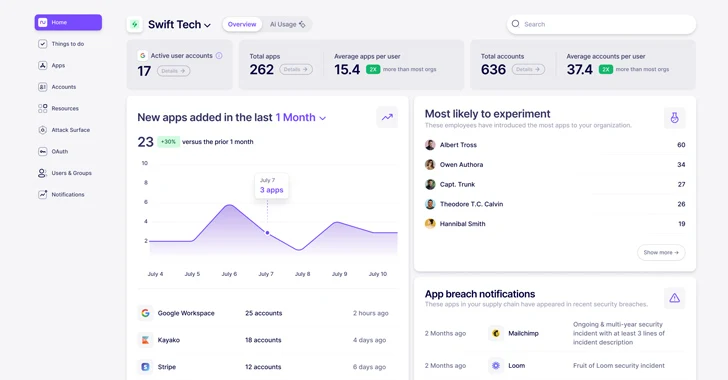
Read More »What is Nudge Security and How Does it Work?
What is Nudge Security and How Does it Work? Jan 24, 2024SaaS Security / Endpoint Security In today’s highly distributed workplace, every employee has the ability to act as their own CIO, adopting new cloud and SaaS technologies whenever and wherever they need. While this has been a critical boon to productivity and innovation in the digital enterprise, it has ...
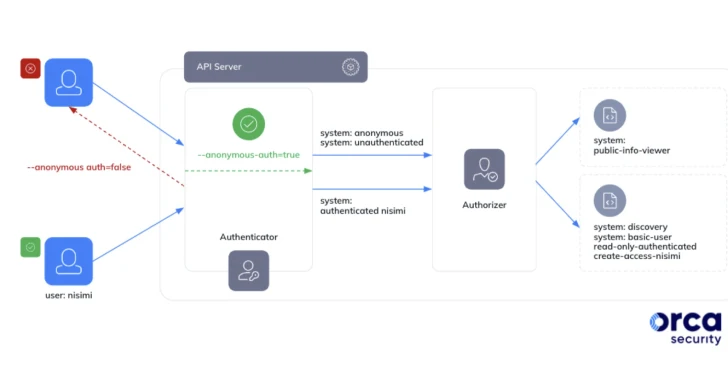
Read More »Google Kubernetes Misconfig Lets Any Gmail Account Control Your Clusters
Google Kubernetes Misconfig Lets Any Gmail Account Control Your Clusters Jan 24, 2024NewsroomCloud Security / Kubernetes Cybersecurity researchers have discovered a loophole impacting Google Kubernetes Engine (GKE) that could be potentially exploited by threat actors with a Google account to take control of a Kubernetes cluster. The critical shortcoming has been codenamed Sys:All by cloud security firm Orca. As many ...
Read More »MGM Resorts breached by ‘Scattered Spider’ hackers: sources
MGM Resorts breached by ‘Scattered Spider’ hackers: sources By Zeba Siddiqui and Christopher Bing SAN FRANCISCO/WASHINGTON – A hacking group named Scattered Spider brought down the systems of the $14 billion gaming giant MGM Resorts International this week, two sources familiar with the matter said, as U.S. law enforcement officials started a probe into the breach. Several MGM systems remained ...
Read More »Apple-backed study finds rise in data breaches
Apple-backed study finds rise in data breaches In the first nine months of 2023, U.S. data breaches increased by 20% compared to the full year 2022, according to a new study that was commissioned by Apple . The iPhone maker paid for the study, which was conducted by Massachusetts Institute of Technology Professor Stuart E. Madnick, about a year after ...
Read More » Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India